Democratic Participation
Posted by KatrinVerclas on Jun 26, 2008
MobileActive.org wants to hire you! If you are a cracker-jack researcher and writer, we want you for research and stories from around the world about mobiles for social impact. Some data entry on organizations and projects around the world using mobile phones to make the world a better place are also part of the job. Online and telephone research, interviews, writing reports and blog posts.
Must be a thorough researcher, and persuasive and clear writer. Living and working experience in developing country/ies a must. This is an ideal position for journalism graduate student with a great interest in mobile tech, or for a technologist interested in the social implications of the mobile revolution. Location in New York preferred but could be done from anywhere IF it's the right person. Fluency in Spanish or Arabic a great plus. Some travel will be supported.
Send a resume, cover letter explaining why we should hire you, and at least TWO published pieces pertaining to this or a related subject matter of at least 300-500 words. Send your materials to katrin [at] mobileactive [dot] org. Search is open until we find the perfect candidate(s), so hurry.
Posted by BrettMeyer on Aug 27, 2007
Much was made of a poll conducted by Zogby International and Rock the Vote just before the 2004 Presidential election. The poll, taken solely over mobile phones, showed John Kerry with a significant lead over George W. Bush. The predictive failure of this groundbreaking poll may be due to the fact that while only 2.3% of the 18- to 29-year-old poll respondents said they did not plan to vote, U.S. census data shows that the actual turnout by the youngest voting blocks was much lower than the national average of 64%, with participation at a mere 47% among those age 18 to 24.
Posted by KatrinVerclas on Aug 14, 2007
We are pleased to welcome Bart Lacroix to MobileActive.org. He will be writing an occasional blog on AfricaNews' Voices of Africa project, an experiment in mobile citizen reporting. AfricaNews currently has three citizen reporters covering stories in their using mobile countries, phones to produce video footage, written reports and photographs.
Using GPRS-enabled phones, on-the-ground citizens reporters don’t need an internet connection at all - only mobile coverage - to send video, voice, and text. The Voices of Africa is deploying reporters in Ghana, South Africa, and Kenya to date who are using Nokia E61i phones to send in their stories. These countries have, admittedly, better mobile coverage than others, so are good for this pilot project. Bart will tell us how it's going, what citizens are reporting on, and what they are learning about content and technical production before sacaling up the project.
A bit of background from AfricaNews' press release:
Posted by KatrinVerclas on Aug 12, 2007
In Sierra Leone's national election today, 500 election observers at polling stations around the country are reporting on any irregularities via SMS with their mobile phones. Independent monitoring of elections via cell phone is growing aqround the world, spearheaded by a few innovative NGOs.
The story starts in Montenegro, a small country in the former Yugoslavia. On May 21, 2006 the country saw the first instance of volunteer monitors using SMS, also known as text messaging, as their main election reporting tool. A Montenegrin NGO, the Center for Democratic Transition (CDT), with technical assistance from the National Democratic Institute (NDI) in the United States, was the first organization in the world to use text messaging to meet all election day reporting requirements.
Posted by KatrinVerclas on Mar 05, 2007
Gerry Jackson reports on Media Helping Media about the radio station SW Radio Africa outsisde of London that is sending sms headlines about news in Zimbabwe to it's subscriber base of about 2,000 mobile users. Jackson writes:
"We generate news headlines on a daily basis anyway - so this is just another way of using what already exists.
It’s nice and cost effective for any additional donor because there is only the one cost, actually sending the texts. In two months we’ve built up an address database of about 2,000 mobile phone numbers. Like many, Zimbabweans truly love their mobile phones and of course what we’re banking on is the virus effect.
We also get up to 100 requests a day to be added to the service so it’s growing rapidly. What becomes interesting is what business model to use?
Posted by AnneryanHeatwole on Jan 02, 2012
Welcome to a very mobile 2012! Last year mobiles were at the forefront of protests, citizen journalism, disaster recovery and relief, environmental issues, and more – and brought up questions of security and privacy along the way. Check out our new page dedicated to MobileActive's 2011; the Year in Review pulls together our best content from the year in one easy location.
From the launch of The Mobile Media Toolkit (a great resource for reporters, citizen journalists, and media organizations that want to use mobile technology in their work) and our increased focus on security and privacy with the SaferMobile initiative, we've set the groundwork for big changes in 2012.
Keep in contact with MobileActive through Twitter, Facebook, our discuss list, or our newsletters at MobileActive.org and (for all of you reporters and citizen journalists) at the Mobile Media Toolkit. We hope that everyone has a safe and happy New Year, and we are excited for what 2012 holds. Thanks for being part of the MobileActive community!
Posted by MelissaLoudon on Dec 22, 2011
Vibe burst onto the scene following reports that protesters were using it to coordinate with each other at the recent Occupy Wall Street demonstrations and camps.
As a smartphone app for anonymous broadcast messaging, Vibe is going after an important idea. In fact, it’s been promoted as an anonymous version of Twitter. Anyone with the app can post - there are no accounts - and users are able to limit the lifetime of the messages (from a few minutes to a few days) and the location to which they are broadcast (from a few meters to anywhere).
Vibe is clearly a useful tool. Some of the ways it has apparently been used include asking anonymous questions at a conference, and communicating with neighbours about local events. The ‘anonymity’ of not having to create an account may be perfectly adequate for these situations. However, when it comes to its use by activists - where it is being promoted as an appropriate tool for people with serious security implications should their identify be revealed - we need to delve deeper into promises of anonymity.
In the case of Vibe, our analysis revealed some serious concerns. Some of these have come up in other reviews as well.
Posted by EKStallings on Dec 19, 2011
Beyond ICT4D: New Media Research in Uganda data sheet 674 Views
Author:
Balunywa , Ali, Guido van Diepen, Wouter Dijkstra, Kai Henriquez, Ben White
Abstract:
This paper is a collection of five ethnographic reports examining the role of ICT in Uganda. The first is not particulalrly mobile focused and looks at how those who have access to internet in Uganda use it. The second report is about the ways ICT is changing print media. The third report focuses on the the opportunities ICT present for civil society and non-governmental groups. The next report outlines the way the ICT sector in Uganda was developed. The last report examines ways that ICT may be used in government accountability.
Posted by EKStallings on Dec 19, 2011
SMS Engagement in Pakistan: A Practical Guide for Civil Society, the Humanitarian Sector, and Government data sheet 1019 Views
Author:
Linton Williams, Jim, Alex Gilchrist
Abstract:
Mobile phones are approaching ubiquity in Pakistan. Allowing low cost access to community members across class, linguistic and geographical boundaries, the mobile phone can be an effective tool to communicate with ordinary people in Pakistan, as well as to learn from them, and even collaborate with them. This guide provides a research-driven and practical guide for using SMS to do so. It is intended for both Pakistani and international institutions, whether in government, civil society or the humanitarian sector. It represents the findings of its authors only, and, it is hoped, is the first draft of a collaborative document, to which many of its readers might contribute.
This document is intended to provide an understanding both of the range of technical options available for SMS-based communications, and of the ways in which campaigns should be conceived and executed in light of the scope and character of both SMS use and phone use in Pakistan.
It also makes the argument that SMS provides an opportunity to do more with mobilebased communications than simple announcements and polling, useful activities though they are. It argues that the conversational nature of SMS, in Pakistan and elsewhere, allows
Posted by AnneryanHeatwole on Dec 16, 2011
FailFaire – where it's okay to admit the mistakes. MobileActive hosted another round of FailFaire, bringing together practitioners, developers, donors, and students involved in the use of technology for social change development to discuss what's usually swept under the rug – project failure. The event is an open space to discuss those projects that went wrong in our field fostering a sense of learning from mistakes and knowledge sharing. The latest FailFaire in New York brought together eight practitioners to present their failed projects and what they learned along the way. Take a look at this FastCompany article about the NYC FailFaire for some background.
So, here we bring you...
Posted by KatrinVerclas on Dec 14, 2011
Editors Note: We started Failfaire almost two years ago to create a space where it was ok to be honest in our field of "tech for social change," and admit that many projects that we all undertake do not succeed. Today is yet another Failfaire here in New York where practitioners come together to discuss how and why our projects failed. We will be writing about this tomorrow to give you more on the #fails presented, but in the meantime were absolutely astounded today to see the following blog post from Daraja about their Maji Matone project. It takes guts (and foresight) to admit so publicly that this project has not succeeded. We wrote about Maji Matone here before. The project was designed to provide local accountability for water services by way of local, grassroots monitoring via SMS. The post below was oroginally published on Daraja's blog here and is reposted here with Daraja's gracious permission. We are grateful for the post, and for the honesty.
Maji Matone hasn't delivered. Time to embrace failure, learn, and move on
It is no secret that Daraja's Maji Matone programme has not lived up to expectations. In particular, despite considerable resources spent on promotional work - printing and distributing posters and leaflets, as well as extensive broadcasts on local radio - we haven't had the response from the community that we had hoped for. A six month pilot in three districts resulted in only 53 SMS messages received and forwarded to district water departments (compared to an initial target of 3,000). So we've made a decision - to embrace failure, learn and share lessons from the experience, and to fundamentally redesign the programme.
Admitting failure in this way is easy to support in theory, but much harder to do in practice. It may be
accepted practice in the for-profit world, but it's uncomfortable for a donor-dependent NGO. Would it be easier to continue half-heartedly with a programme that isn't working or close it down quietly and hope that nobody notices? Of course it would. But those approaches would not benefit anyone, wasting money and missing out on valuable opportunities to learn. So we're taking a different tack, embracing and publicising our failures, and trying to make sure we (and others) learn as much as possible from the experience
Posted by AnneryanHeatwole on Dec 03, 2011
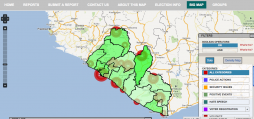
On November 8, 2011, the Liberian President Ellen Johnson Sirleaf won her re-election campaign following a contentious runoff vote. In the October 11 general election, neither of the top two presidential candidates secured a majority vote –Johnson Sirleaf received 43.9% of votes and opposition candidate Winston Tubman received 32.7% of the nation’s votes. Johnson Sirleaf and Tubman were scheduled to participate in a November 8 runoff election; however, Tubman boycotted it saying that the first elections had been unfair; a claim international election observers dispute. As the only candidate, Sirleaf won the runoff despite a low 37.4% of eligible voters coming out for the second round (compared to more than 70% for the first round).
In light of the election’s tumult, MobileActive.org spoke to the National Democratic Institute and Ushahidi Liberia to learn more about their respective work in the country encouraging transparency and fairness through election monitoring and citizen reporting.
The National Democratic Institute and Ushahidi in the 2011 Liberian Elections
Elections can be rigged in many ways, and voter fraud is varied. For instance, ballots can be changed or manipulated, voters can be influenced through intimidation or bribes, violence can shut down polling stations, or ballots can be changed after the election before the results are announced. Technical difficulties can also influence an election by preventing voters from casting their votes or having those votes accurately counted; difficulties could include long lines, failure to open a polling place on time, or a lack of necessary supplies.
| Technology in the 2011 Liberian Elections: Mobiles, Monitoring, and Mapping data sheet 1783 Views |
| Countries: |
Liberia
|
Posted by VivianOnano on Nov 21, 2011
User Guide | Data Integrity data sheet 707 Views
Abstract:
FrontlineSMS is a software platform that enables structured communication via text messaging, using only a computer and a mobile phone or GSM (Global System for Mobile) modem. The platform enables two-way messaging between users and groups of people via mobile networks without the need for an Internet connection.
The purpose of this guide is to provide FrontlineSMS users designing, implementing, and monitoring programs with data integrity concerns in mind with a data integrity framework. The guide is intended to help users to understand, analyze, and address the vulnerabilities, risks and threats that can affect the integrity of the information communicated through the FrontlineSMS platform.
Posted by ccarlon on Nov 18, 2011
The Power of Social Media in Developing Nations data sheet 1234 Views
Abstract:
On January 28, 2011, Egypt’s President, Hosni Mubarak, took the drastic and unprecedented step of shutting off the Internet for five days across an entire nation. His reason for doing so was simple: to halt the flow of communication and coordinated assembly taking place over social media platforms, like Facebook and Twitter. That Mubarak took this desperate step — which cost Egypt an estimated $90 million and outraged the international community — demonstrates the incredible power of social media. Mubarak’s decision to shut off the Internet took place after three days of demonstrations by tens of thousands of Egyptians. Although the demonstrations were centered in Cairo’s Tahrir Square (or “Liberation Square”), there were also substantial demonstrations in Alexandria, Mansoura, and Suez. The protesters expressed outrage over several issues, including state corruption, police brutality, and economic oppression. Their demand was clear: President Hosni Mubarak must leave the country.
Various groups, including April 6 Youth Movement, We Are All Khaled Said, National Association for Change, and Kefaya led a coordinated effort using social media platforms, including Facebook and Twitter, to spread a revolutionary message. Prior to the first day of protest, 85,000 Egyptians pledged on Facebook to attend “Revolution Day.” Similarly, April 6 Movement had over 90,000 members during the protests, and We Are Khaled Said had over 40,000 Facebook fans. In the two weeks leading up to and including the first few days of the protest, Egyptians created 32,000 Facebook groups and 14,000 Facebook pages. It is likely that a substantial number of the five million Facebook users in Egypt were in some way encouraged to attend the protests.
Posted by kelechiea on Nov 18, 2011
The Role of Mobile-Enabled Social Media in Social Development data sheet 686 Views
Abstract:
A number of countries recently experienced protests organized by citizens that were in pursuit of accountability and openness from government. It was witnessed that social media played a highly important role in those events; among others, continuously providing updated information, establishing human networks, forming opinions, mobilizing people, and taking concerted actions.
Of course, social media is not the sole reason that made the events happen. However, it can be at least said that the general public were encouraged to move into the actions for their enhanced well-being. From a broader perspective, those occurrences also showcase that Information & Communications Technologies (ICTs) can help enhance social development among people.
This short note seeks to develop analysis on the role of social media in social development, in the wake of the increasing diffusion of mobile phone Internet access.
Posted by AnneryanHeatwole on Nov 07, 2011
How can you share information across rural areas with limited or non-existent Internet connections? This is the question that Awaaz.De, an India-based organization that uses interactive-voice-response (IVR) systems to share information on mobile phones, is working to answer.
Co-created by Neil Patel and Tapan Parikh, both at the University of California at Berkeley, Awaaz.De is used by organizations to share information with voice as the primary channel. This could, for instance, take the form of a question and answer service, voice discussion forums, voice surveys, and automated calls.
Because of the open-ended structure of the Awaaz.De platform, the platform has been adapted by very different organizations. Labor Voices uses Awaaz.De to allow migrant workers to review jobs and employers in a voice database; the Development Support Centre uses the service to provide information to small-scale farmers as part of the Avaaj Otalo project (covered by MobileActive.org here), and Galli Galli Sim Sim (the Indian version of Sesame Street) uses the service to allow pre-school teachers to share teaching experiences and information about educational activities.
According to Patel in a post on the ICT 4 Community Health Worker discussion list, there are now eight organizations using Awaaz.De. These organizations have, together, produced more than 100,000 calls from about 10,000 unique callers.
| Calling It In: Awaaz.De Provides A Voice-Based Information Platform data sheet 1667 Views |
| Countries: |
India
|
Posted by AnneryanHeatwole on Oct 27, 2011
Today's Mobile Minute brings you coverage on India's mobile growth, smartphones in Asia, the relationship between social media and mobile phones in America, Nokia's global sales report, and the rise of open data projects in the United Kingdom.
- Reuters reports that mobile subscriptions in India are on the rise; in August alone mobile phone operators added 7.34 million new subscribers, bringing the country's total number of mobile subscriptions to 865.71 million. However, now that roughly 70% of the country's population has a mobile phone, the number of new subscribers is rising more slowly than last year as the market becomes more saturated.
- The mobile and smartphone market in the Asia-Pacific region is growing rapidly, and Cellular News has the breakdown of current and projected sales: "The smartphone market is [...] expected to have healthy growth, with 24% share in total handset shipments in 2011, up from 17% in 2010. Smartphone shipments in Asia will see a significant growth of 56% in 2011, which indicates the growing demand for smartphones in emerging Asian markets. Smartphone shipments in Asian markets will see a boost for Android-based smartphones, with market share increasing to 52% in 2011, up from 16% in 2010. As a result, the combined market share of Samsung and HTC, the leading Android-based smartphone makers in Asia, will swell from 11% in 2010 to 24% in 2011."
Posted by AnneryanHeatwole on Oct 25, 2011
Following this weekend's Tunisian elections, the world is looking to the Middle East to see how new democracies are born. But in many countries with emerging democracies, fraud and corruption can taint the credibility of elections, and the public's trust in the fairness and validity of election results. We have long argued that technology - mobile technology in particular - can play a key role in helping to ensure fair and accurate voting processes and results. However, data has been missing to make that point more definitively.
In areas where much of the voting process isn't digitized, using technology can help mitigate vote tampering and incorrect results. Additionally, SMS reports of vote tabulation from polling stations by trained election observers can be an effective way of limiting voting fraud and corruption, and has been used in different elections around the world. In Lebanon's 2009 elections, roughly 2500 volunteer citizen observers reported from a statistically significant number of polling station incidence reports throughout election day. In Nigeria, 2011 Project Swift Count deployed 8000 trained election observers across the country to report on the elections, including election results from polling stations directly, using SMS.
| Tech in Election Monitoring: Fighting Fraud and Corruption, one Picture at a Time data sheet 2006 Views |
| Countries: |
Afghanistan
|
Posted by ccarlon on Oct 21, 2011
Global Mapping of Technology for Transparency and Accountability data sheet 1368 Views
Author:
Avila, Renata, Hazel Feigenblatt, Rebekah Heacock, and Nathaniel Heller
Abstract:
As internet and mobile phone use increases, technology is transforming the field of transparency and accountability making it an increasingly dynamic space across the globe. Technology is helping to improve citizen participation in decision-making and producing new ways of identifying public service challenges through processes such as ‘data mashing’.
This paper documents current trends in the way technology is being used to promote transparency in different parts of the world. It reviews over 100 projects from across Africa, Asia, Europe and Latin America, examining how new technologies are re-energising traditional methods. In particular, it focuses on how these new technologies are helping to engage different actors from citizens, media, authorities and the private sector.
Our research finds promising success stories alongside less accomplished examples. The authors argue that a key element of successful technology use in transparency and accountability efforts is their speed – both in execution and in stimulating change. Well-designed efforts produced relevant and usable information that can be used to demand accountability quickly. Technology for transparency and accountability tools need not be sophisticated, but it does need intelligent design that is relevant to the local context. Projects also have a better chance of effectively producing change when they take a collaborative approach, sometimes involving government.
Posted by ccarlon on Oct 14, 2011
Gibberbot data sheet 1008 Views
Organization that developed the Tool:
Problem or Need:
Gibberbot is designed for people who need to chat securely. If you and the person you are communicating with are both able to use it, secure chat can be used as a replacement for email and text messaging.
Gibberbot should work on any Android phone. It’s probably best for users who are reasonably comfortable chatting and handling their phone, and it’s only currently available in English.
Brief Description:
Gibberbot is an instant messaging app for Android phones, developed by The Guardian Project. Gibberbot implements off-the-record messaging (OTR). Off-the-record messaging is a way to conduct an instant messaging conversation with the following attributes
- Encryption. An eavesdropper cannot read your messages
- Authentication. You can verify the identity of the person you’re chatting to - or at least of the account they are using.
- Deniability. It is not possible for a third party to prove that a particular user sent or received a particular message.
- Perfect forward secrecy. It is not possible for an attacker to decrypt a previous conversation, even if he/she obtains the encryption keys used to encrypt it.
Gibberbot can also use Orbot to route your chats over the Tor network. This prevents an observer from following the source and destination of your messages (effectively, from knowing you are chatting) and provides a way to circumvent web censorship that may involve chat servers being blocked.
Off-the-record messaging only works when both parties in the conversation are using it. This means both parties need to use Gibberbot, another mobile app, or chat software that supports it. Currently Gibberbot is the only option we know of for mobile phones. Off-the-record plugins are available for several PC chat programs, including Pidgin (Windows and Linux), Adium (Mac), Trillian (Windows) and Miranda (Windows).
Tool Category:
App resides and runs on a mobile phone
App resides and runs on a server
Key Features :
- When used with Orbot, Gibberbot combines the security, privacy and anonymity provisions of off-the-record messaging with the additional anonymous browsing and circumvention protection of the Tor network.
- Gibberbot is currently the only implementation of off-the-record messaging for mobile phones that we are aware of.
- The code for Gibberbot is open source and freely available for download - there are no costs involved except your airtime while chatting.
- The project encourages user feedback through a mailing list, feedback form on their website, twitter account and IRC channel.
Is the Tool's Code Available?:
Is an API available to interface with your tool?:
Posted by ccarlon on Oct 14, 2011
For many, mobile devices are an indispensable tool for storing and sharing increasingly sensitive information. Contacts, emails, and mobile browsing history can easily be compromised without taking the proper measures to ensure that that information is safely in the right hands... and out of the wrong ones. Newly added to our mDirectory are the following how-to guides on securing mobile email, mobile anonymity, backups, and data deletion from our SaferMobile team:
- Securing Your Mobile Email - This guide catalogs the different tactics you can take to keep mobile email safe. It covers email security basics, TLS/SSL enabling, and email encryption. The guide also provides customized tactics and suggestions for Android, Blackberry, iPhone, and Nokia/Symbian phones.
- Mobile Tools for Backups, Data Deletion and Remote Wipe - Anyone who has ever had their phone stolen knows how frustrating and potentially dangerous that can be. Here we have a comprehensive review of some of the tools out there for data backup and restore, data deletion, and remote wipe.
For all other materials produced by the SaferMobile team, check out this complete list (and watch for a new SaferMobile site soon!)
Posted by MelissaLoudon on Oct 14, 2011
Mobile Tools for Backups, Data Deletion and Remote Wipe data sheet 1865 Views
Abstract:
Anyone who has had a phone stolen knows the frustration of trying to rebuild your contact list, not to mention data on the phone that is unrecoverable. Worse, the data stored on your phone can be dangerous in the wrong hands. In addition to being able to impersonate you to your mobile contacts, consider the risk of an attacker who has access to some of all of the following:
- Your saved contacts - names, phone numbers, perhaps also email addresses and physical addresses
- Call logs - calls made and received
- Stored text messages
- A calendar with your appointments, or a task list
- Your mobile email
- Your web browser with stored passwords
- Photos, video and sound recordings stored on the phone and memory card
- Data stored by applications - notes, social networking contacts and posts
Three kinds of tools can lessen the pain of losing your mobile data, and limit your risk should your phone be lost or stolen.
- Backup and restore tools allow you to save a backup of contacts and other data stored on your phone
- Data deletion tools can be used to ‘clean’ a phone completely before disposing of it, giving it away or travelling to a location where you are worried it could be stolen or confiscated
- Remote wipe tools are set up so that if your phone is lost or stolen, you are able to clean it remotely, deleting sensitive data. Many remote wipe tools also allow you to track the phone provided it has not been turned off.
Anyone who has had a phone stolen knows the frustration of trying to rebuild your contacts list, not to mention data on the phone that is unrecoverable. Worse, the data stored on your phone can be dangerous in the wrong hands. In addition to being able to impersonate you to your mobile contacts, consider the risk of an attacker who has access to some of all of the following:
- Your saved contacts - names, phone numbers, perhaps also email addresses and physical addresses
- Call logs - calls made and received
- Stored text messages
- A calendar with your appointments, or a task list
- Your mobile email
- Your web browser with stored passwords
- Photos, video and sound recordings stored on the phone and memory card
- Data stored by applications - notes, social networking contacts and posts
Three kinds of tools can lessen the pain of losing your mobile data, and limit your risk should your phone be lost or stolen.
Posted by MelissaLoudon on Oct 14, 2011
Securing your Mobile Email data sheet 2116 Views
Abstract:
Email wasn’t designed with security in mind. Unless you take steps to protect your communication, emails are sent in plain text - and so are your email account username and password.
At the same time, if you and your recipient are taking the appropriate security precautions, mobile email can be a secure and reliable alternative to other forms of mobile communication. If you have data service for your mobile, encrypted email can replace text messaging, and if you aren’t able to access a website securely to upload content - photos or videos for example - getting it to a trusted contact as an email attachment can be a safer alternative.
Email wasn’t designed with security in mind. Unless you take steps to protect your communication, emails are sent in plain text - and so are your email account username and password.
At the same time, if you and your recipient are taking the appropriate security precautions, mobile email can be a secure and reliable alternative to other forms of mobile communication. If you have data service for your mobile, encrypted email can replace text messaging, and if you aren’t able to access a website securely to upload content - photos or videos for example - getting it to a trusted contact as an email attachment can be a safer alternative.
This article suggests the following tactics for improving the security of your mobile email:
Email security basics
Even if you’re not using encrypted email, you can take some basic precautions to improve your email security. For example
Posted by ccarlon on Oct 13, 2011
Blacknoise: Low-fi Lightweight Steganography in Service of Free Speech data sheet 1063 Views
Abstract:
Censorship of communications is a widespread, current practice in various countries with repressive governments in order to prevent or restrict speech; political speech in particular. In many cases state-run telecommunications agencies including those providing internet and phone service, actively filter content or disconnect users in defense of incumbents in the face of widespread criticism by citizens.
In this paper I present Blacknoise, a system which uses commodity low-cost mobile telephones equipped with cameras, and takes advantage of their lowfidelity, noisy sensors in order to enable embedding of arbitrary text payloads into the images they produce. These images can then be disseminated via MMS, Bluetooth, or posting on the Internet, without requiring a separate digital camera or computer to perform processing.
Posted by MelissaLoudon on Oct 13, 2011
Mobile Anonymity and Censorship Circumvention: How to Browse the Web Anonymously On Your Phone data sheet 3553 Views
Abstract:
If you don’t want someone to know that you were accessing a particular web site (or that you were accessing it at a particular time, such as when inflammatory content was posted), you need to anonymize your mobile browsing. Depending on how your network is set up, the site you are accessing may be able to see and keep a record of your IP address. Your network administrator, Internet Service Provider and/or Mobile Network Operator can see and keep records of the IP addresses of both your Internet-connected mobile device and the sites you are accessing. IP addresses can nearly always be linked to a geographic location, whether a zip code or a city, and your ISP or mobile network provider can link your IP to your individual device.
The first part of this article - Using HTTPS for Secure Mobile Browsing - describes how mobile browsing over HTTPS provides:
- encryption for you data during transmission
- verification of the identity of the remote site
However, using HTTPS does not hide your identity. If you don’t want someone to know that you were accessing a particular web site (or that you were accessing it at a particular time, such as when inflammatory content was posted), you need to anonymize your mobile browsing. Depending on how your network is set up, the site you are accessing may be able to see and keep a record of your IP address. Your network administrator, Internet Service Provider and/or Mobile Network Operator can see and keep records of the IP addresses of both your Internet-connected mobile device and the site you are accessing. IP addresses can nearly always be linked to a geographic location, whether a zip code or a city, and your ISP or mobile network provider can link your IP to your individual device.
Organisations and countries that block websites can do so by blocking communication to and from specific IP addresses. For this reason, anonymizing your browsing is also the first step to circumventing Internet censorship.
This article describes two tactics for anonymous browsing and censorship circumvention - using a proxy, and using a mobile version of the circumvention tool Tor. Both are used on cpmputers as well as mobile devices. Specific tools for mobile phones are described in the second part of the article.