safermobile
Posted by KatrinVerclas on Aug 11, 2011
Telcos or mobile operators have been in the news lately, implicated in the suppression of communications, tracking and surveillance of pro-democracy and human rights activists, and in their close collaboration with repressive regimes and their security apparatuses around the world. Now there is a new initiative spearheaded by advocacy organization Access Now that advocates for mobile operators to sign a set of five principles focused on human and democratic rights in return for their licenses.
Nothing New: How Cozy Telcos Are With Repressive Regimes
Vodafone's recent decision to shut down its communications network in Egypt and the delivery of pro-government propaganda via text message over its network made the news but that was just the tip of the iceberg. The examples abound: Uganda operators monitored and blocked certain SMS keywords in the advent of the recent election there, pro-Zanu propaganda is widely delivered over Zimbabwean operator networks, Russian mobile operators agreed to 'police' the Internet and their networks at the behest of the Russian government, and Belarussian telcos routinely supply information to the security police, including location information of known political activists.
This close collaboration of many operators with repressive states has been going on for some time but there is now a new activist movement forming, holding telcos accountable and to a higher standard. Led by activist shareholders and advocacy organizations like Access, activists point out that the negative publicity of this corporate behavior carries financial implications that pose a risk to telco investors.
Posted by KatrinVerclas on Jul 27, 2011
We are developing a global database of SIM cards registrations by country, and we need your help. Please fill out this short survey. We ask you a few questions about a particular country's requirements.
Note: This survey will not track identifying information. We will publish the complete database on the site shortly with the data that we have gathered to date. The survey is here. Thanks!
Photo courtesy flickr user bfishshadow.
Posted by MelissaLoudon on Jul 11, 2011
HTTP, the Hypertext Transfer Protocol, is the data communication protocol you use when you broswe the web - as you probably know if you've noticed that website addresses usually begin with http://. HTTPS is the secure version of HTTP, which you might have seen being used for sensitive transactions like online banking and online shopping. When you are using the secure part of a site, the web address will begin with https://.
When using your mobile phone for sensitive communications, it is important to ensure that your online activities - whether researching or reading about an issue, sending an email, writing a blog post or uploading photos - are done over a secure connection. There are three elements of secure web browsing:
Posted by MelissaLoudon on Jun 30, 2011
Smartphones (iPhone, Android, Blackberry, Windows Mobile, Symbian) and many feature phones allow you to download and install mobile applications (“apps”). Apps do many useful things. However, some apps (and other types of software, such as your mobile operating system) can also present security risks. These include:
-
Apps and other software may have access to information stored on or generated by your phone.
-
Apps and other software may have the ability to transmit this information using your phone’s Internet connection.
Malicious apps or other mobile software installed on your mobile device can expose you to the following risks:
-
Your conversations may be listened to or recorded without your knowledge.
-
Your text messages, emails and web traffic may be monitored and logged.
-
Data stored on your phone (contacts, calendar entries, photos and video) may be accessed or copied.
-
Passwords stored or entered on your phone may be stolen and used to access your online accounts.
-
Your location may be tracked, even when your phone is switched off.
With smartphones gaining market share, malicious apps are beginning to pose a serious threat. In an article titled “Your Apps Are Watching You”, the Wall Street Journal tested popular iPhone and Android apps, and found that of 101 apps tested, 56 transmitted a unique identifier for the phone without informing the user or asking for consent. 47 apps also transmitted the phone’s location, while 5 sent age, gender or other personal details to various companies. The App Genome Project reports that 28% of all apps in the Android Market and 34% of all free apps in the Apple App Store have the capability to access location, while 7.5% of Android Market apps and 11% of Apple App Store apps have the capability to access users’ contacts.
It can be very difficult to tell which apps are safe and which are not. App behaviours that might not bother most users, such as transmitting the phone’s location to an advertising server, can be unacceptable to people with higher privacy and security requirements.
This article offers suggestions on how to assess risks to security and privacy posed by apps.
Posted by SaferMobile on Jun 29, 2011
Despite the smartphone craze of the past 5 years, featurephones are still king in much of the world. From the perspective of activists, rights defenders, and journalists, they cannot be ignored. And feature phones have plenty of built-in capability to help users stay safer. During the course of our research, we've uncovered valuable features that even the most experienced users may not be aware of.
As a part of SaferMobile, a project of MobileActive.org, we've focused on documenting the most important ways that a user can lock down a mobile handsets. No external apps or special tools are required, just a charged battery. We've condensed these tips into single-page, device-specific reference guides for a variety of makes & models that get straight to the point. And yes, we made sure to cover smartphones and featurephones.
Posted by VivianOnano on Jun 29, 2011
Mobile Application Security data sheet 959 Views
Posted by SaferMobile on Jun 17, 2011
Safer Twitter data sheet 3163 Views
Twitter is a way to get your messages to a wider audience. However, you should know that from any platform (computer or mobile phone), it is not a secure method of communicating sensitive information. Consider the following guidelines:
- Your Tweets should only contain information you want to widely and publicly share. This should be public information that can be freely distributed by you, your organization, and your supporters, without any risk to individuals or organizational operations.
- Even if you protect your tweets so that only followers can see them, followers can easily retweet your messages, or access them over an insecure connection.
Posted by MarkWeingarten on Jun 14, 2011
According to the Wall Street Journal, “[Data produced by the use of mobile phones] generates immense commercial databases that reveal the ways we arrange ourselves into networks of power, money, love and trust.” As mobile phone use increases and applications become increasingly sophisticated, the volume of mobile data we create continues to grow at an incredible rate, creating new possibilities and posing new challenges to notions of privacy.
Businesses want this data for marketing. Congress wants to regulate it. Activists and privacy advocates want to ensure that it is not used to compromise their safety or freedoms. Meanwhile, projects such as UN Global Pulse want to use information gleaned from mobile phone use to detect and prevent slow-onset humanitarian crises. We invite you to join us on the evening of June 30th for our next New York City-based Mobile Tech Salon as we explore these tough questions:
- How do we determine socially beneficial uses for mobile data?
- How can the safety, security, and privacy of individuals be respected while using mobile data to benefit them?
- How can our mobile data be effectively aggregated and anonymized? Or can’t it?
Posted by SaferMobile on Jun 10, 2011
A Guide to Mobile Security Risk Assessment data sheet 2309 Views

You are an activist, rights defender, or journalist. You use a mobile device. And you work in sometimes risky situations in your country.
This guide will help you implement mobile security practices in your work. It will help you assess the particular risks that face you and then assist you in developing a plan to mitigate those risks.
We have previously published a Mobile Risk Primer that describes general security vulnerabilities associated with mobile technology and communication. Read it!
Throughout this guide, we'll also highlight the fictitious case of Asima, a blogger and activist in Egypt. Examples of how Asima might complete the assessment worksheet and create a security plan for her work are highlighted in this guide.
Asima lives in Cairo, Egypt and is a blogger and an activist. She used to maintain a blog on Blogspot, but now mostly uses Facebook and Twitter to follow current events, to share information, and to communicate with colleagues. She tweets from her mobile phone while in traffic and at cafes and protests and from her computer when she is at work or at home. |
Posted by MarkWeingarten on Jun 10, 2011
We've heard much recently about information that is being tracked by mobile phone companies (see our recent post) and app developers. However, there are more overt security threats that are potentially more dangerous.
One of these threats is referred to as either a “roving bug” or a “remote listening” application. It is essentially the same concept as a conventional audio bug, except that it requires no hardware other than a smartphone. Once installed, remote listening software enables a 3rd party to call a phone, activate its speakerphone capabilities, and secretly transmit any sounds picked by its microphone to another phone number, where it can be monitored and recorded.
Posted by MarkWeingarten on May 24, 2011
SMSTester for Android data sheet 1129 Views
Posted by SaferMobile on May 18, 2011
One of the main goals of the SaferMobile project is to release software tools that allow activists and rights defenders to use their mobile phones as network monitors and sensors. The goal is to help them, and the mobile developers, human rights organizations and people on the street they work with, to monitor network performance and proactively detect blocking, filtering and censorship. SMSTester is the first tool we are publicly releasing within this category, and it is free, freely licensed and open-source. Our first trial run with Short Message Service Tester (SMSTester) was completed in April 2011. The results are written up here.
Posted by SaferMobile on May 16, 2011
Activists, rights defenders, and journalists use mobile devices for reporting, organizing, mobilizing, and documenting. We have written about many of these uses for years now, describing how mobile phones provide countless benefits to activists and rights defenders. Mobile tech is relatively low cost and allows for increased efficiencies and vast reach, for example. But, there is a darker side.
Mobile Phones present specific risks to rights defenders, journalists, and activists. We believe that is is critically important to know that mobile communication is inherently insecure and exposes rights defenders and those working in sensitive environment to risks that are not easy to detect or overcome. (We provide an overview of those risks in this Primer, for instance)
To address mobile safety and security for rights defenders, we are introducing SaferMobile, to help activists, human rights defenders, and journalists assess the mobile communications risks that they are facing, and then use appropriate mitigation techniques to increase their ability to organize, report, and work more safely.
What is SaferMobile?
- Online and offline educational and tactical resources (risk evaluation tools, case studies, how-to guides, security tool reviews);
- Trainings and curricula for use in various countries and with different constituencies;
- Specific mobile security software focused on the needs of rights defenders, activists, and journalists.
As will all that we do, we believe that there certain values and principles that are paramount in this work. For SaferMobile, we are following these principles:
- We believe that skilled, trained, and knowledgeable activists, journalists, and rights defenders are key to democratic changes. We also believe that the smart and effective use of technology constitutes an integral piece of their skill set.
- The better activists, journalists, and rights defender are able to work, the more safely they are able to organize and communicate, the more likely it is that their work is effective and heard.
- We are committed to accessible, useful, actionable, and technically accurate and secure content, materials, and software.
- We are also committed to describing technological vulnerabilities in terms that non-technical users can easily understand.
- We work with activists on the ground to ensure that the content we produce addresses real uses and risks.
- We also seek responsive connections between activists and security professionals so that both are more able to assess and respond to changing risks.
- Lastly, we are maintaining information that reflects current security risks and technological vulnerabilities and is vetted for security and technological accuracy by knowledgeable experts.
Roadmap and Process
The SaferMobile project is just beginning its second Phase. Phase 1 included needs assessment with users and peers – activists, rights defenders, journalists, technologists, security experts, and mobile developers. Through this research, we outlined plans for web content, training curriculum and tools (software) and are now creating these pieces in Phase 2 of the project (May-August 2011).
Our approach is iterative and open – we work as a team to develop ideas and welcome review and comments from peers. We maintain a wiki for this initial phase that will act as a living lab for content and code as we develop both.
Posted by MarkWeingarten on May 10, 2011
Apple’s release of version 4.3.3 of its iOS operating system “..kills iPhone tracking”, according to a recent article. After nearly three weeks of public attention on this issue, this news will perhaps appease some iPhone fans but is not likely to end the debate over what users should know and control about their smartphones’ location tracking abilities. Like Apple, Google’s Android and Microsoft’s Windows Phone systems have also recently come under fire, though important differences exist in the way each company collects and uses location-based information.
We have reviewed recent articles and research on each of these mobile operating systems’ location tracking capabilities and will describe the various claims made and the research undertaken to test these claims.
Posted by SaferMobile on Apr 25, 2011
NOTE: This article was updated with an addendum and additional data.
Inspired by Michael Benedict's original blog post on monitoring SMS delivery reliability in Tanzania and recent reports of SMS keyword blocking in Uganda, MobileActive.org set out to replicate Michael's work - and add to it. SMS is such a crucial part of many mobile projects and just day-to-day life across the developing world, yet there’s a lack of public knowledge of mobile network operator interdependency, latency, and reliability (how mobile network operators work together to transmit SMS, the lag time between sending and receiving a message, and the guarantee that a message will reach its recipient).
Michael's post got us thinking: Can this type of experiment be replicated without extra hardware required (GPRS modems, etc.)? After a few quick brainstorming sessions at the OpenMobile Lab in New York, we created an alpha version of a mobile application that recreates a number of latency tests. It’s far from perfect - and there is still plenty of work to be done - but we’re confident that this project will lead us to extremely valuable data about the transparency and reliability of SMS on mobile networks.
SMSTester - The App
SMSTester is a simple Android app that allows a user create a set of keywords to be sent as SMS messages. This allows the user to explore differences in latency for any type of message - from basic, everyday text like ‘milk’ or ‘newspaper’ to politically inflammatory text such as ‘revolution.’ We then set up a logging mechanism to timestamp and record each SMS as it is sent (from the sender side) or received (on the receipt side). By comparing the sent and received timestamps, we’re very easily able to calculate message latency from one SIM to another.
Initial Deployment
We deployed SMSTester in a test in Egypt a few weeks ago. As this was the initial trial for a fully untested application, we were careful. While we did run our tests across a number of local mobile operator networks, we kept the test volume small enough to keep us under the radar (for now!). Our test methodology included:
- Testing across all three major mobile operator networks in Egypt: Etisalat, Mobinil, and Vodafone
- Consistent keyword test bed containing both ‘safe’ and ‘political’ terms, where ‘safe’ refers to everyday vocabulary and ‘political’ refers to politically sensitive words
- Language coverage across both English and Arabic
- Roughly 270 messages successfully sent, received and analyzed
What We Looked For And Why
The main focus of our analysis was SMS delivery latency, delay, or more generally, delivery failures. There are plenty of anecdotal stories of seemingly random delays lasting multiple hours or even days in many countries where we work. While network congestion and growing infrastructure are often to blame for SMS unreliability, there are also legitimate concern that delays may be an indication of deliberate message filtering and monitoring. What has emerged is an environment in which activists and human rights defenders are unable to clearly understand what networks - and what behavior - is safe or hazardous for themselves or their contacts. The end goal of this research, put simply, is to change this paradigm. Rumors of keyword filtering are not helpful; what is helpful is any evidence of surveillance.
This small experiment is just a start, of course. Our hypothesis is that keyword filtering and other malicious behavior on the part of mobile network operators may manifest in the form of increased message latency or overt message blockage. If we could detect any sign of a correlation between message content and delivery with just some initial testing in-country, this would be a great first step towards our overall goal. However it’s very important to note that while message latency or failure may be indicative of bad behavior on the part of the carries, it could be due to any number of contributing factors and is by no means an implication of foul play. For now we’re merely hypothesizing.
Results
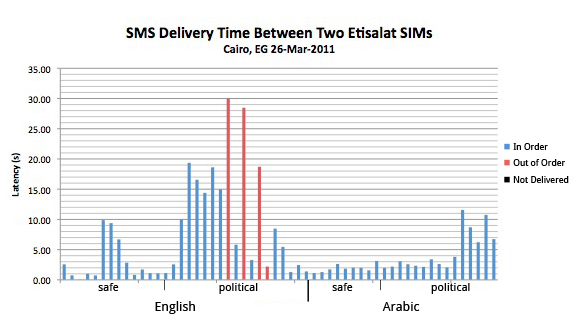
Despite the minor bugs discovered, we gathered very valuable information about message latency in Egypt during this trial. The most valuable data was on the Etisalat network (also known as the Emirates Telecommunications Corporation), based in the UAE. The majority of the data we recovered from this trial was between an Etisalat SIM and other Egyptian networks. (Note: This was the result of inadvertent data loss for other test scenarios and we did not specifically target Etisalat).
Main Conclusions
Big Caveat (READ THIS!): Given the small sample size of this test, it should be noted that none of these conclusions are definitive. In fact, the very nature of such a small sample size warrants much further investigation.
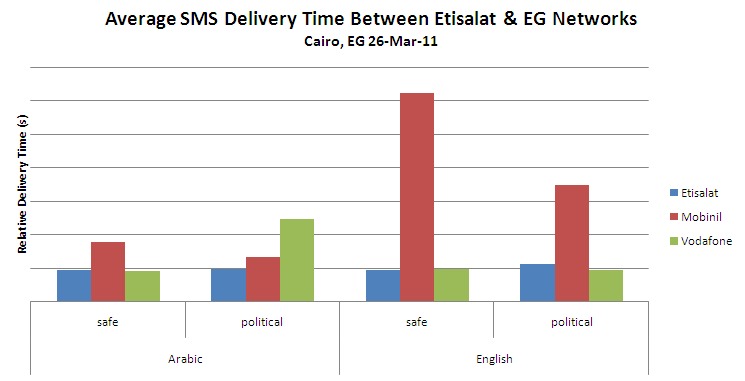
(1) Delivery between Etisalat & Mobinil networks warrants further investigation. As shown below, the delivery time for English language text messages from Etisalat to Mobinil is significantly greater than delivery time to any other network, for both English and Arabic texts. This may be due to any number of network delays, and it may also be indicative of English language filtering by one or both of the mobile network operators.
(2) Delivery time of politically sensitive English messages on Etisalat warrants further investigation. The chart below shows that politically sensitive English messages sent across the Etisalat network were delivered with significantly more latency than others, with the possible exception of politically sensitive Arabic messages. In addition, each of the three messages that were delivered out of order fell into this category. Similar to the above conclusion, this may be indicative of specific filtering on behalf of Etisalat.
| SMSTester - Monitoring SMS Delivery (and Keyword Filtering, Possibly) data sheet 4643 Views |
| Countries: |
Egypt
|
Posted by KatrinVerclas on Mar 29, 2011
Please join us on Friday, April 1 in NYC! To celebrate April Fools Day and to highlight mobile phone & digital network insecurities, the Guardian Project and MobileActive.org are hosting "Don't be Fooled", part of the new SaferMobile initiative. This hackday will showcase mobile tools to enhance security, profile GP's open-source tools and feature a room for face-to-face conversations about mobile security.
Do to the intimate size of the venue, we are caping RSVPs at 30: 20 "developers / hackers" who want to learn about developing secure mobile phone services and 10 practitioners who want to root their phones / learn about mobile security. Please put your name here!
Location: Open Mobile Lab, 127 W 27 St, Suite 702, NYC
Time: Friday, 1 April 2011 from 9:30 till 5:00. Beer O'Clock from 5:00 till 7:00.
Hashtag: #safermobile
The Guardian Project (@guardianproject) aims to create easy to use apps, open-source firmware MODs, and customized, commercial mobile phones that can be used and deployed around the world, by any person looking to protect their communications and personal data from unjust intrusion and monitoring.
MobileActive.org (@MobileActive) connects people, organizations, and resources using mobile technology for social change. Our global network of practitioners and technologists are working
Photo Courtesy flickr user juli ryan
Posted by MelissaUlbricht on Mar 10, 2011
Safer Photos: How to Remove Location Information from Mobile Images data sheet 6658 Views
In a previous post, we described how to add location information to mobile content, including images and stories. For some reports, location information adds value, context, and interest to venue-specific reports. But today, we talk about how to remove that same location information. This is also detailed, step by step, in this screencast.