A primer on mobile security risks for activists, rights defenders, and journalists. includes tips on how to protect yourself.
Activists, rights defenders, and journalists use mobile devices and communications for reporting, organizing, mobilizing, and documenting. Mobiles provide countless benefits -- relatively low cost, increased efficiencies, vast reach -- but they also present specific risks to rights defenders and activists.
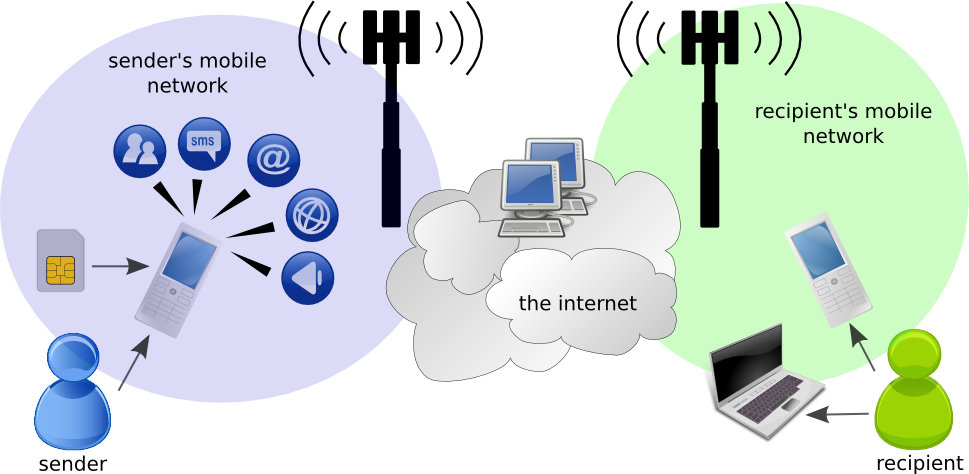
Additionally, information about other mobile uses, such as your photos or video, your data, the Internet sites you visit from your phone, and your physical location, are stored on your device and often logged by your mobile network. (The above graphic shows a schematic overview of the layers of the mobile networks to give you sense of the different elements that make up communications between two phones.)How much is this putting you at risk? This Overview will help you evaluate your level of risk in regard to your mobile communications.
Part I describes security vulnerabilities associated with mobile phone technology and the risks they pose to you - the information held by your mobile network operator (MNO or operator), the information stored on your phone, and the risks related to unauthorized use.
Part II discusses common phone capabilities - voice, SMS/text messaging, web browsing, mobile email, mobile photos and video, and smartphone apps. We describe the safety risks these pose for you and give you tips on how to minimize them.
How to use this overview
We use little pictures/icons in this guide to make it easier for you to follow.
 This icon connotes techniques that you can implement yourself to increase your safety as you use a mobile device.
This icon connotes techniques that you can implement yourself to increase your safety as you use a mobile device.
 Watch out for this icon. There are many areas of vulnerability, both on mobile device and network levels, that you should be aware of. Many of these are hard to protect against. Use caution!
Watch out for this icon. There are many areas of vulnerability, both on mobile device and network levels, that you should be aware of. Many of these are hard to protect against. Use caution!
Part I: General Mobile Risks
This section describes general characteristics associated with mobile phone technology - the information held by your mobile network operator, the information stored on your phone, and the risks unauthorized use of this information may pose to you.
 Your mobile service is operated by your mobile network operator. As it manages your communication, it is also able to record certain types of messages you send, as well as information about your communication activities and your device. Note that none of these risks is easy to mitigate. The motto here is: The more you know, the more you can make smart choices regarding your mobile communications.
Your mobile service is operated by your mobile network operator. As it manages your communication, it is also able to record certain types of messages you send, as well as information about your communication activities and your device. Note that none of these risks is easy to mitigate. The motto here is: The more you know, the more you can make smart choices regarding your mobile communications.
Network records
Network records are vulnerable if you suspect you are being surveilled by someone who could access them. This might be via the legal system (a subpoena, or formal legal demand), an informal government request, or through a corrupt employee of the network operator.
- Any communication your phone has with the mobile network - whether placing or receiving a call, sending a message, browsing the web or just remaining connected - includes identifying information about the phone and the SIM card. There are two numbers that are important
- The IMEI is a number that uniquely identifies the phone - the hardware.
- The IMSI is a number that uniquely identifies the SIM card.
Security Risks
When your phone is switched on, the network knows your location, triangulated from the cell towers nearby that record your phone’s signal. Your location might be accurate to as much as a few meters in a densely populated area but only to a few hundred meters in a rural area with few cell towers. If you make or receive a call or send or receive a text message, your location at that time is stored in network records. Note that this is a function of the mobile network, not any nefarious surveillance. All networks triangulate your signal. This is important to remember as this information can be used against you!
Monitoring/Eavesdropping
- The contents of your text messages are visible in plain text and also stored in network records.
- Text messages (and emails if sent unencrypted) with certain keywords can be blocked and the sender singled out.
- Calls can be monitored and recorded by network personnel, and recordings may be passed (legally or illegally) to someone outside the operator. Your calls may be listened to during or after the call.
- Internet traffic can be monitored and recorded. Network operators can see what websites you access and may also see data you send and receive. Again, this information can be recorded for later use and may be passed on to someone else outside the operator.
- Any unusual encrypted communication (to anything other than widely used websites such as Gmail, for example) may appear suspicious to the network operator. For example, simply sending encrypted text messages over a mobile network can arouse suspicion and single you out.
Disrupted access
- Your mobile communication relies on service from the mobile network operator. It is easy for your operator to disrupt or disable your service.
- Governments can request that mobile operators shut down all or parts of their network - for example, during elections or to stem protest action.
- Your mobile number or the IMEI or IMSI numbers associated with your services may be selectively disabled.
- Specific websites you are trying to access via your mobile phone may be blocked.
|
Physical and Remote Access to Your Phone
Mobile phones are easily lost, stolen, or taken from you. It is therefore important for you to understand what an attacker might learn when your phone is taken from you.

Security Risks
Data on the Phone and SIM Card
If someone else has your phone, it is easy to link your personal identity to your device and all sensitive and compromising data on the phone through SIM registration, IMEI, and IMSI numbers. Consider the following ways that you may be storing sensitive information on your phone:
- The phone’s address book can store your contacts (names, telephone number, email, etc), and anyone with access to your phone can see these contacts.
- The phone stores your call history - who you called and received calls from, and the time calls were made.
- The phone stores SMS text messages you have sent or received as well as draft messages. It is possible to recover messages even if you have deleted them from the phone memory.
- Any applications you use, such as a calendar or to-do list, store data on the phone or on a memory card.
- Photos you have taken using the phone camera are stored on the phone or memory card. Most phones store the time the photo was taken and may also include location information and the make and model of the phone.
- If you use a web browser on your phone, your browsing history (sites visited), and bookmarks may be stored.
- If you use an email app, your emails, like any other application data, may be stored on the phone.
- All of this data that is stored is not easily destroyed or wiped permanently and can be recovered with data forensics methods. Other people might be able to recover data even if it appears deleted to you.
Unauthorized use
Unauthorized use, either because someone has taken possession of the phone, or because compromising software has been installed, is a risk for any type of phone.
- For many phones, it is possible for an attacker to gain unauthorized access remotely if the attacker can install an application on the device. To do this, an attacker might trick you into downloading a file from the Internet or open an infected MMS, or take advantage of having temporary physical access to the device.
- Phone theft is another way to get access to the device. If your phone is ever out of your possession for an extended period of time and is returned to you, use it with extreme caution.
- While a PIN code might slow a thief down, there are many ways to get around entering the PIN to access data. It’s best not to rely on it to protect you.
- Unauthorized use allows an attacker to impersonate you to contacts who identify you by your phone number or email address.
- With readily available software, a full phone image (a copy of all your data and activity records) can be made for subsequent analysis.
- Unauthorized use can include making expensive calls.
|
Part II: Specific Mobile Use Risks
This section describes risks of using your mobile phone for specific types of communication, media capture, and data storage -- voice, SMS/text messaging, web browsing, mobile email, mobile photos and video, and smartphone apps.
Voice: This Call May Be Recorded...
Voice is used for person-to-person calling and personal voicemail (if available), but can also be part of an automated system. For example, Interactive Voice Response (IVR) systems might operate a hotline for reporting incidents of police corruption.

Security Risks
All voice communications can expose you, whether it is by simple eavesdropping by someone physically near to you or by tracking call recipients and times at the network level. Here are some risks to consider and ways to minimize these risks.
Eavesdropping/Recording calls
- As with any conversation, you could be overheard or recorded by someone nearby.
- Your conversation could be eavesdropped or recorded by an app installed on your phone without your knowledge.
- Voice calls are encrypted between the handset and the cell tower. However, various sophisticated attacks are possible against mobile networks, particularly older standards (the GSM standard, still the predominant standard in the world, is more vulnerable than 3G). For example, hardware that impersonates a GSM base station is commercially available.
Persistent Records
- The details of your call (whom you called, at what time, for how long) are stored by the network even if the content is not. Unless you have taken specific precautions, you and the person you call are using phones that have been linked to you by both the IMEI number (the handset identifier) and the IMSI (the SIM card identifier).
- Voicemail messages are stored by the mobile network operator and should not be considered secure, even when protected by a personal PIN.
- Interactions with an Interactive Voice Response (IVR) system are only as secure as the system itself. Be sure that the organization or entity running the system is trustworthy, technically competent, and will not allow your calls to be monitored or recorded.
- Any phone use reveals your location to the network operator. The stored record of your activity (calls, texts, data use) places you in a particular place at a particular time.
|
SMS/Text Messaging
Like voice, SMS, also referred to as text messaging, can be used between individuals - for conveying short information, getting someone to call you back, or just keeping in touch. Automatic systems for one-to-many texting are also useful, for example, in mobilizing a large group or getting news out. Many-to-one/data collection systems are also popular to help aggregate incident reports, solicit opinions, or collect some kinds of routine data.

Security Risks
- SMS messages are sent in plain text. They are not encrypted, so the content is not hidden or disguised in any way. Anyone who intercepts the messages (with the help of the mobile network operator or by listening for traffic in a particular network cell) can read your SMS
- Mobile network operators keep records of SMSs sent through their network. This includes details of date and time sent, details about the sender and recipient, as well as the unencrypted contents of the message.
- Sent or received messages stored on a phone or SIM are vulnerable if the phone or SIM is lost or stolen.
- It is possible for mobile apps to access sent and received text messages that are stored on your phone.
|
Web Browsing
The mobile web isn’t just for browsing, although looking for information or news reports is one of its main uses. If you are using the web version of an online service such as Gmail, Twitter, Facebook), or if you are blogging or tweeting from your phone, you may also be using the mobile web. Certain smartphone apps also use the web to send or receive data.

Security Risks
- Unless you are using HTTPS (you can tell by looking at the site address - it should begin with https:// and not just http://), your traffic is not encrypted. A curious attacker on the network can use a packet sniffing tool to see:
- What sites you are accessing
- Content you are uploading/downloading
- Some mobile web browsers don’t support HTTPS at all, meaning your account credentials (user name and passwords) and any queries are transmitted in the clear and unencrypted all the time.
- Your web access sessions are recorded, with time and date, by the mobile network operator.
- Unless you are using a traffic anonymizing service like>Tor, the network operator can see both the source (your phone) and destination (the website you are visiting) of all your browsing. This information may also be logged (stored) by the network operator.
- Some mobile web browsers - notably Opera Mini - route the pages you see through their server to optimize them for mobile viewing. Even if your connection to the page is secure, they see data you send and receive in plain text.Opera Mini on the iPhone has the same problem. Older versions of Opera Mini (prior to Opera Mini Basic v.3) also send data in plain text between their server and the website you are browsing.
- If you use the browser on your phone to save passwords to websites you use often, remember that anyone with physical access to your phone can potentially see those passwords and access these same websites on your behalf.
- Remember that websites, as well as the Internet service provided by your mobile network, can be unavailable at times. This could be because of technical problems or a malicious attack.
|
Mobile Email
Mobile email can be accessed in two ways.
- Through your phone’s browser using a webmail provider (Gmail, Hotmail and Yahoo, for example). Everything we’ve said about secure web browsing above also applies to email access through your phone browser.
- Using a dedicated email app that you might install or that might come pre-installed on the phone. The way these apps work can vary quite a bit and so can their security.

Security Risks
- If you access your email through the phone’s browser and do not use HTTPS, your message is sent in plain text and can be read by the mobile network operator and potentially by malicious attackers on the open Internet.
- Even if you use HTTPS, the network operator can see the site you are accessing, as well as the date and time of the transaction, your location at the time, and identifying information about your phone. This information may also be logged/stored.
- Email headers - email addresses of the sender and recipient, email subject - are never encrypted even when using an encrypted email protocol like PGP.
- The recipients of your email may have security vulnerabilities on their side, and the message content and your identity may be revealed by them.
|
Photos, Video and MMS

Security Risks
- The date and time you took a photo or video are saved as part of the descriptive information for each media item. The phone model may also be saved. This descriptive information is called EXIF data.
- Location information may also be saved as part of EXIF data.
- If you upload photos or videos to a website (Twitter, Facebook, Flickr, YouTube, your blog), the descriptive information may be preserved. Anyone viewing your media could see where, when, and with what phone you created it. Some sites strip this information off during the upload process (at the time of writing, Facebook was one that did), but it’s never worth relying on this.
- If you send photos or video as an email attachment, the descriptive information is always preserved.
- MMS, like SMS, can be intercepted and viewed by the network operator. Information about your phone (identifying numbers, location) is also available to the network operator
- Although mobile viruses and malicious mobile software are rare, there are cases where MMS has been used to install these on unsuspecting feature phones.
- Phones with cameras can pose a surveillance risk. If someone has unauthorized remote access to the phone, the camera can potentially be remotely activated to take pictures without a user’s knowledge.
|
Security for Smartphones

Security Risks
- Be very wary of open public WiFi networks - the kind that do not require a password, for example in coffee shops or hotels. It is very easy for an attacker on the same network to collect anything sent in plain text. It is also easy to eavesdrop HTTPS connections (a “man-in-the-middle” attack).
- WiFi networks that require a WEP key (you’ll see this when you connect) are also not very secure, and should be avoided.
- Smartphones with always-on Internet connectivity and GPS make you easier to track accurately.
- Apps can easily have malicious code hidden within them that collect and transmit your personal information without your knowledge.
|
To listen to an audio recording of this piece, click here. Thank you to Ashiyan Rahmani-Shirazi (@ashiyan) for the sound recording.
A primer on mobile security risks for activists, rights defenders, and journalists. includes tips on how to protect yourself.
Activists, rights defenders, and journalists use mobile devices and communications for reporting, organizing, mobilizing, and documenting. Mobiles provide countless benefits -- relatively low cost, increased efficiencies, vast reach -- but they also present specific risks to rights defenders and activists.

Additionally, information about other mobile uses, such as your photos or video, your data, the Internet sites you visit from your phone, and your physical location, are stored on your device and often logged by your mobile network. (The above graphic shows a schematic overview of the layers of the mobile networks to give you sense of the different elements that make up communications between two phones.)How much is this putting you at risk? This Overview will help you evaluate your level of risk in regard to your mobile communications.
Part I describes security vulnerabilities associated with mobile phone technology and the risks they pose to you - the information held by your mobile network operator (MNO or operator), the information stored on your phone, and the risks related to unauthorized use.
Part II discusses common phone capabilities - voice, SMS/text messaging, web browsing, mobile email, mobile photos and video, and smartphone apps. We describe the safety risks these pose for you and give you tips on how to minimize them.
How to use this overview
We use little pictures/icons in this guide to make it easier for you to follow.
 This icon connotes techniques that you can implement yourself to increase your safety as you use a mobile device.
This icon connotes techniques that you can implement yourself to increase your safety as you use a mobile device.
 Watch out for this icon. There are many areas of vulnerability, both on mobile device and network levels, that you should be aware of. Many of these are hard to protect against. Use caution!
Watch out for this icon. There are many areas of vulnerability, both on mobile device and network levels, that you should be aware of. Many of these are hard to protect against. Use caution!
Part I: General Mobile Risks
This section describes general characteristics associated with mobile phone technology - the information held by your mobile network operator, the information stored on your phone, and the risks unauthorized use of this information may pose to you.
 Your mobile service is operated by your mobile network operator. As it manages your communication, it is also able to record certain types of messages you send, as well as information about your communication activities and your device. Note that none of these risks is easy to mitigate. The motto here is: The more you know, the more you can make smart choices regarding your mobile communications.
Your mobile service is operated by your mobile network operator. As it manages your communication, it is also able to record certain types of messages you send, as well as information about your communication activities and your device. Note that none of these risks is easy to mitigate. The motto here is: The more you know, the more you can make smart choices regarding your mobile communications.
Network records
Network records are vulnerable if you suspect you are being surveilled by someone who could access them. This might be via the legal system (a subpoena, or formal legal demand), an informal government request, or through a corrupt employee of the network operator.
- Any communication your phone has with the mobile network - whether placing or receiving a call, sending a message, browsing the web or just remaining connected - includes identifying information about the phone and the SIM card. There are two numbers that are important
- The IMEI is a number that uniquely identifies the phone - the hardware.
- The IMSI is a number that uniquely identifies the SIM card.
Security Risks
When your phone is switched on, the network knows your location, triangulated from the cell towers nearby that record your phone’s signal. Your location might be accurate to as much as a few meters in a densely populated area but only to a few hundred meters in a rural area with few cell towers. If you make or receive a call or send or receive a text message, your location at that time is stored in network records. Note that this is a function of the mobile network, not any nefarious surveillance. All networks triangulate your signal. This is important to remember as this information can be used against you!
Monitoring/Eavesdropping
- The contents of your text messages are visible in plain text and also stored in network records.
- Text messages (and emails if sent unencrypted) with certain keywords can be blocked and the sender singled out.
- Calls can be monitored and recorded by network personnel, and recordings may be passed (legally or illegally) to someone outside the operator. Your calls may be listened to during or after the call.
- Internet traffic can be monitored and recorded. Network operators can see what websites you access and may also see data you send and receive. Again, this information can be recorded for later use and may be passed on to someone else outside the operator.
- Any unusual encrypted communication (to anything other than widely used websites such as Gmail, for example) may appear suspicious to the network operator. For example, simply sending encrypted text messages over a mobile network can arouse suspicion and single you out.
Disrupted access
- Your mobile communication relies on service from the mobile network operator. It is easy for your operator to disrupt or disable your service.
- Governments can request that mobile operators shut down all or parts of their network - for example, during elections or to stem protest action.
- Your mobile number or the IMEI or IMSI numbers associated with your services may be selectively disabled.
- Specific websites you are trying to access via your mobile phone may be blocked.
|
Physical and Remote Access to Your Phone
Mobile phones are easily lost, stolen, or taken from you. It is therefore important for you to understand what an attacker might learn when your phone is taken from you.

Security Risks
Data on the Phone and SIM Card
If someone else has your phone, it is easy to link your personal identity to your device and all sensitive and compromising data on the phone through SIM registration, IMEI, and IMSI numbers. Consider the following ways that you may be storing sensitive information on your phone:
- The phone’s address book can store your contacts (names, telephone number, email, etc), and anyone with access to your phone can see these contacts.
- The phone stores your call history - who you called and received calls from, and the time calls were made.
- The phone stores SMS text messages you have sent or received as well as draft messages. It is possible to recover messages even if you have deleted them from the phone memory.
- Any applications you use, such as a calendar or to-do list, store data on the phone or on a memory card.
- Photos you have taken using the phone camera are stored on the phone or memory card. Most phones store the time the photo was taken and may also include location information and the make and model of the phone.
- If you use a web browser on your phone, your browsing history (sites visited), and bookmarks may be stored.
- If you use an email app, your emails, like any other application data, may be stored on the phone.
- All of this data that is stored is not easily destroyed or wiped permanently and can be recovered with data forensics methods. Other people might be able to recover data even if it appears deleted to you.
Unauthorized use
Unauthorized use, either because someone has taken possession of the phone, or because compromising software has been installed, is a risk for any type of phone.
- For many phones, it is possible for an attacker to gain unauthorized access remotely if the attacker can install an application on the device. To do this, an attacker might trick you into downloading a file from the Internet or open an infected MMS, or take advantage of having temporary physical access to the device.
- Phone theft is another way to get access to the device. If your phone is ever out of your possession for an extended period of time and is returned to you, use it with extreme caution.
- While a PIN code might slow a thief down, there are many ways to get around entering the PIN to access data. It’s best not to rely on it to protect you.
- Unauthorized use allows an attacker to impersonate you to contacts who identify you by your phone number or email address.
- With readily available software, a full phone image (a copy of all your data and activity records) can be made for subsequent analysis.
- Unauthorized use can include making expensive calls.
|
Part II: Specific Mobile Use Risks
This section describes risks of using your mobile phone for specific types of communication, media capture, and data storage -- voice, SMS/text messaging, web browsing, mobile email, mobile photos and video, and smartphone apps.
Voice: This Call May Be Recorded...
Voice is used for person-to-person calling and personal voicemail (if available), but can also be part of an automated system. For example, Interactive Voice Response (IVR) systems might operate a hotline for reporting incidents of police corruption.

Security Risks
All voice communications can expose you, whether it is by simple eavesdropping by someone physically near to you or by tracking call recipients and times at the network level. Here are some risks to consider and ways to minimize these risks.
Eavesdropping/Recording calls
- As with any conversation, you could be overheard or recorded by someone nearby.
- Your conversation could be eavesdropped or recorded by an app installed on your phone without your knowledge.
- Voice calls are encrypted between the handset and the cell tower. However, various sophisticated attacks are possible against mobile networks, particularly older standards (the GSM standard, still the predominant standard in the world, is more vulnerable than 3G). For example, hardware that impersonates a GSM base station is commercially available.
Persistent Records
- The details of your call (whom you called, at what time, for how long) are stored by the network even if the content is not. Unless you have taken specific precautions, you and the person you call are using phones that have been linked to you by both the IMEI number (the handset identifier) and the IMSI (the SIM card identifier).
- Voicemail messages are stored by the mobile network operator and should not be considered secure, even when protected by a personal PIN.
- Interactions with an Interactive Voice Response (IVR) system are only as secure as the system itself. Be sure that the organization or entity running the system is trustworthy, technically competent, and will not allow your calls to be monitored or recorded.
- Any phone use reveals your location to the network operator. The stored record of your activity (calls, texts, data use) places you in a particular place at a particular time.
|
SMS/Text Messaging
Like voice, SMS, also referred to as text messaging, can be used between individuals - for conveying short information, getting someone to call you back, or just keeping in touch. Automatic systems for one-to-many texting are also useful, for example, in mobilizing a large group or getting news out. Many-to-one/data collection systems are also popular to help aggregate incident reports, solicit opinions, or collect some kinds of routine data.

Security Risks
- SMS messages are sent in plain text. They are not encrypted, so the content is not hidden or disguised in any way. Anyone who intercepts the messages (with the help of the mobile network operator or by listening for traffic in a particular network cell) can read your SMS
- Mobile network operators keep records of SMSs sent through their network. This includes details of date and time sent, details about the sender and recipient, as well as the unencrypted contents of the message.
- Sent or received messages stored on a phone or SIM are vulnerable if the phone or SIM is lost or stolen.
- It is possible for mobile apps to access sent and received text messages that are stored on your phone.
|
Web Browsing
The mobile web isn’t just for browsing, although looking for information or news reports is one of its main uses. If you are using the web version of an online service such as Gmail, Twitter, Facebook), or if you are blogging or tweeting from your phone, you may also be using the mobile web. Certain smartphone apps also use the web to send or receive data.

Security Risks
- Unless you are using HTTPS (you can tell by looking at the site address - it should begin with https:// and not just http://), your traffic is not encrypted. A curious attacker on the network can use a packet sniffing tool to see:
- What sites you are accessing
- Content you are uploading/downloading
- Some mobile web browsers don’t support HTTPS at all, meaning your account credentials (user name and passwords) and any queries are transmitted in the clear and unencrypted all the time.
- Your web access sessions are recorded, with time and date, by the mobile network operator.
- Unless you are using a traffic anonymizing service like>Tor, the network operator can see both the source (your phone) and destination (the website you are visiting) of all your browsing. This information may also be logged (stored) by the network operator.
- Some mobile web browsers - notably Opera Mini - route the pages you see through their server to optimize them for mobile viewing. Even if your connection to the page is secure, they see data you send and receive in plain text.Opera Mini on the iPhone has the same problem. Older versions of Opera Mini (prior to Opera Mini Basic v.3) also send data in plain text between their server and the website you are browsing.
- If you use the browser on your phone to save passwords to websites you use often, remember that anyone with physical access to your phone can potentially see those passwords and access these same websites on your behalf.
- Remember that websites, as well as the Internet service provided by your mobile network, can be unavailable at times. This could be because of technical problems or a malicious attack.
|
Mobile Email
Mobile email can be accessed in two ways.
- Through your phone’s browser using a webmail provider (Gmail, Hotmail and Yahoo, for example). Everything we’ve said about secure web browsing above also applies to email access through your phone browser.
- Using a dedicated email app that you might install or that might come pre-installed on the phone. The way these apps work can vary quite a bit and so can their security.

Security Risks
- If you access your email through the phone’s browser and do not use HTTPS, your message is sent in plain text and can be read by the mobile network operator and potentially by malicious attackers on the open Internet.
- Even if you use HTTPS, the network operator can see the site you are accessing, as well as the date and time of the transaction, your location at the time, and identifying information about your phone. This information may also be logged/stored.
- Email headers - email addresses of the sender and recipient, email subject - are never encrypted even when using an encrypted email protocol like PGP.
- The recipients of your email may have security vulnerabilities on their side, and the message content and your identity may be revealed by them.
|
Photos, Video and MMS

Security Risks
- The date and time you took a photo or video are saved as part of the descriptive information for each media item. The phone model may also be saved. This descriptive information is called EXIF data.
- Location information may also be saved as part of EXIF data.
- If you upload photos or videos to a website (Twitter, Facebook, Flickr, YouTube, your blog), the descriptive information may be preserved. Anyone viewing your media could see where, when, and with what phone you created it. Some sites strip this information off during the upload process (at the time of writing, Facebook was one that did), but it’s never worth relying on this.
- If you send photos or video as an email attachment, the descriptive information is always preserved.
- MMS, like SMS, can be intercepted and viewed by the network operator. Information about your phone (identifying numbers, location) is also available to the network operator
- Although mobile viruses and malicious mobile software are rare, there are cases where MMS has been used to install these on unsuspecting feature phones.
- Phones with cameras can pose a surveillance risk. If someone has unauthorized remote access to the phone, the camera can potentially be remotely activated to take pictures without a user’s knowledge.
|
Security for Smartphones

Security Risks
- Be very wary of open public WiFi networks - the kind that do not require a password, for example in coffee shops or hotels. It is very easy for an attacker on the same network to collect anything sent in plain text. It is also easy to eavesdrop HTTPS connections (a “man-in-the-middle” attack).
- WiFi networks that require a WEP key (you’ll see this when you connect) are also not very secure, and should be avoided.
- Smartphones with always-on Internet connectivity and GPS make you easier to track accurately.
- Apps can easily have malicious code hidden within them that collect and transmit your personal information without your knowledge.
- Mobile Use by Micro & Small Enterprises, Wedding Cakes and more
Digital Customization: Mobile Wedding venues in Chicago are offering apps or mobile-responsive websites where couples can customize their venue layout, pick décor themes, and even select lighting moods.
This level of customization ensures the couple can envision and shape their special day in real-time.
|
To listen to an audio recording of this piece, click here. Thank you to Ashiyan Rahmani-Shirazi (@ashiyan) for the sound recording.
 Protect Yourself
Protect Yourself
Post new comment