This article contains information to help you understand and mitigate mobile security risks related to Twitter. As always, remember that risks are context-specific, and depend on the environment you work in as well as whether you are communicating sensitive information. For more information on risk assessment, please review the Guide to Mobile Security Risk Assessment.
Twitter is a way to get your messages to a wider audience. However, you should know that from any platform (computer or mobile phone), it is not a secure method of communicating sensitive information. Consider the following guidelines:
- Your Tweets should only contain information you want to widely and publicly share. This should be public information that can be freely distributed by you, your organization, and your supporters, without any risk to individuals or organizational operations.
- Even if you protect your tweets so that only followers can see them, followers can easily retweet your messages, or access them over an insecure connection.

Assess Your Mobile Twitter Risks
General risks associated with Twitter use include:
- Your log-in details are compromised, and someone then accesses your account unauthorized and impersonate you.
- Your identity is exposed if you are identified as the source of your tweets (if you choose to tweet pseudonymously or anonymously).
- Your location while tweeting is known in real time or afterwards through analysis of your use of Twitter on your mobile network.
This article contains information to help you understand and mitigate these risks. As always, remember that risks are context-specific, and depend on the environment you work in as well as whether you are communicating sensitive information. For more information on risk assessment, please review the Guide to Mobile Security Risk Assessment.
How to Access Twitter via MobileWhen you use Twitter from a mobile phone, you may be exposed to additional risks, and should plan your activities accordingly. There are three ways to access Twitter from your mobile phone:
|
Each of the these has different associated risks, and different options for mitigating action.
| Access Method | Risks | Mitigating actions |
| Text messaging (SMS) |
|
|
| Twitter Apps |
|
|
| https://mobile.twitter.com/ through your phone’s web browser |
|
|
 Seven Twitter Security Tips
Seven Twitter Security Tips
1. Protect your account from unauthorized use
Because Twitter feeds are highly public, it is important to prevent unauthorized access to your account. Here are a few ways to protect against another person gaining your login information and impersonating you.
2. Use a strong password for your Twitter account, and keep it safe
A strong password is one that is:
- Not a single dictionary word, consider using a short phrase.
- Not easily guessed by someone with access to your personal details - for example, don’t use your name, the name of a family member, your birth date, address, or hometown.
- Ideally, contains letters and numbers.
- Not re-used for all your accounts on different website
Don’t save your password by checking ‘remember me’ when you log in. Don’t let your web browser store your password. Not having to type your password may be convenient, but this lets anyone with physical access to your device log in as you and post with your account!
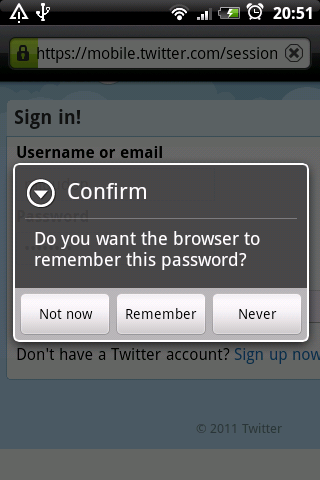
Don’t give your password to third-party applications unless you are sure they are trustworthy. Twitter provides more information on dealing with third-party applications. In particular, be wary of mobile and desktop applications that ask you to log into your Twitter account. Web applications that you access through your browser are usually ok provided the page where you enter your username and password is secure - always look for a lock icon and a web address that starts with https://.
3. Don’t be fooled by fake Twitter login pages
Twitter warns users about the existence of fake login pages, set up to steal usernames and passwords from users in a scam know as ‘phishing’. To protect yourself,
- Always check the web address of the page before entering your username and password
- All legitimate Twitter pages have web addresses ending in ‘Twitter.com’.
- Very rarely, it may be possible for someone to create a fake login page with Twitter’s real web address. Although unlikely, you should be aware of this possiblity, and pay attention to anything that looks different or out of place during the login process. If you suspect your account has been compromised, immediately discontinue us of the account, log out, and, at minimum, change your password.
4. Instead of an app, use your phone’s web browser to access Twitter’s secure site (https://mobile.twitter.com/)
Many Twitter apps send data in plain text rather than over a secure connection. Unless you are sure that the app you are using communicates over HTTPS, consider using your mobile browser to access Twitter’s secure mobile site.
- Your phone’s web browser needs to support HTTPS. Avoid older browsers, particularly Opera Mini Basic 3 and below.
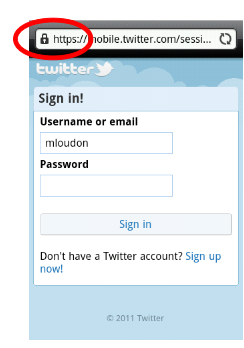
- All your communication with Twitter should display a lock icon to indicate secure browsing, and a web address starting with https:// rather than http://
- Set “always use https” in your Twitter settings but be aware that this setting is not applied when browsing from a phone!
5. Be aware of what information your use of Twitter reveals - to you followers, to your mobile network operator, and to Twitter itself
Tweeting reveals identifying information
- The time of your tweet is visible to anyone with access to your Twitter feed
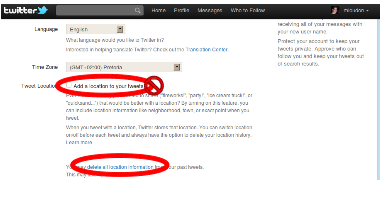
- Twitter allows you to link your tweets to your location. To avoid this information being recorded and shared by Twitter, turn off your “add location to your tweets” under the heading Tweet Location in your settings.
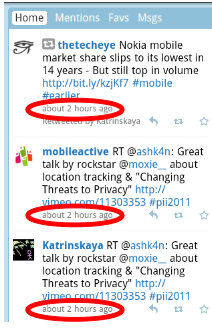
- Identifying information about phones that were accessing Twitter at that time are known to the mobile network operator. This may allow someone with access to both your Twitter feed and the operator’s records to identify you.
6. Twitter can decide to or be forced to hand over information about your account to third parties
Twitter’s privacy policy states the following:
- “We may disclose your information if we believe that it is reasonably necessary to comply with a law, regulation or legal request; to protect the safety of any person; to address fraud, security or technical issues; or to protect Twitter's rights or property.”
- A recent high-profile example is the subpoena issued to Twitter by the US government requiring that identifying information (but not actual tweets) for Twitter accounts related to or following Wikileaks.
7. Always have a backup plan
Twitter can be blocked, or experience extended downtime
Mobile network operators, Internet service providers (ISPs) and governments can block access to certain web services. Twitter is also notorious for periods of downtime. If you think this may affect you, for instance, if you are using Twitter to communicate about emergencies, consider the following tactics:
- Decide on a backup method of communication, and a meeting place
- Have a trusted contact outside the country agree to forward your communications on, either through their own account or with access to yours. Contact them by email or phone.
- Consider using a proxy to access the Internet
- Consider using Orbot (Tor on Android) to hide the source and destination of your communications. Orbot also includes a proxy service that may allow you to access blocked sites.
Security resources at Twitter.com
- Twitter’s Guidelines for Law Enforcement describe the information Twitter has about its users, and the legal procedures involved in someone else gaining access to it.
- Twitter also has a general Privacy Policy. Use the address privacy@twitter.com to ask questions or report concerns.
- There is extensive additional information on the site’s Safety Center page.
This article contains information to help you understand and mitigate mobile security risks related to Twitter. As always, remember that risks are context-specific, and depend on the environment you work in as well as whether you are communicating sensitive information. For more information on risk assessment, please review the Guide to Mobile Security Risk Assessment.
Twitter is a way to get your messages to a wider audience. However, you should know that from any platform (computer or mobile phone), it is not a secure method of communicating sensitive information. Consider the following guidelines:
- Your Tweets should only contain information you want to widely and publicly share. This should be public information that can be freely distributed by you, your organization, and your supporters, without any risk to individuals or organizational operations.
- Even if you protect your tweets so that only followers can see them, followers can easily retweet your messages, or access them over an insecure connection.

Assess Your Mobile Twitter Risks
General risks associated with Twitter use include:
- Your log-in details are compromised, and someone then accesses your account unauthorized and impersonate you.
- Your identity is exposed if you are identified as the source of your tweets (if you choose to tweet pseudonymously or anonymously).
- Your location while tweeting is known in real time or afterwards through analysis of your use of Twitter on your mobile network.
This article contains information to help you understand and mitigate these risks. As always, remember that risks are context-specific, and depend on the environment you work in as well as whether you are communicating sensitive information. For more information on risk assessment, please review the Guide to Mobile Security Risk Assessment.
How to Access Twitter via MobileWhen you use Twitter from a mobile phone, you may be exposed to additional risks, and should plan your activities accordingly. There are three ways to access Twitter from your mobile phone:
|
Each of the these has different associated risks, and different options for mitigating action.
| Access Method | Risks | Mitigating actions |
| Text messaging (SMS) |
|
|
| Twitter Apps |
|
|
| https://mobile.twitter.com/ through your phone’s web browser |
|
|
 Seven Twitter Security Tips
Seven Twitter Security Tips
1. Protect your account from unauthorized use
Because Twitter feeds are highly public, it is important to prevent unauthorized access to your account. Here are a few ways to protect against another person gaining your login information and impersonating you.
2. Use a strong password for your Twitter account, and keep it safe
A strong password is one that is:
- Not a single dictionary word, consider using a short phrase.
- Not easily guessed by someone with access to your personal details - for example, don’t use your name, the name of a family member, your birth date, address, or hometown.
- Ideally, contains letters and numbers.
- Not re-used for all your accounts on different website
Don’t save your password by checking ‘remember me’ when you log in. Don’t let your web browser store your password. Not having to type your password may be convenient, but this lets anyone with physical access to your device log in as you and post with your account!

Don’t give your password to third-party applications unless you are sure they are trustworthy. Twitter provides more information on dealing with third-party applications. In particular, be wary of mobile and desktop applications that ask you to log into your Twitter account. Web applications that you access through your browser are usually ok provided the page where you enter your username and password is secure - always look for a lock icon and a web address that starts with https://.
3. Don’t be fooled by fake Twitter login pages
Twitter warns users about the existence of fake login pages, set up to steal usernames and passwords from users in a scam know as ‘phishing’. To protect yourself,
- Always check the web address of the page before entering your username and password
- All legitimate Twitter pages have web addresses ending in ‘Twitter.com’.
- Very rarely, it may be possible for someone to create a fake login page with Twitter’s real web address. Although unlikely, you should be aware of this possiblity, and pay attention to anything that looks different or out of place during the login process. If you suspect your account has been compromised, immediately discontinue us of the account, log out, and, at minimum, change your password.
4. Instead of an app, use your phone’s web browser to access Twitter’s secure site (https://mobile.twitter.com/)
Many Twitter apps send data in plain text rather than over a secure connection. Unless you are sure that the app you are using communicates over HTTPS, consider using your mobile browser to access Twitter’s secure mobile site.
- Your phone’s web browser needs to support HTTPS. Avoid older browsers, particularly Opera Mini Basic 3 and below.
- All your communication with Twitter should display a lock icon to indicate secure browsing, and a web address starting with https:// rather than http://
- Set “always use https” in your Twitter settings but be aware that this setting is not applied when browsing from a phone!

5. Be aware of what information your use of Twitter reveals - to you followers, to your mobile network operator, and to Twitter itself
Tweeting reveals identifying information
- The time of your tweet is visible to anyone with access to your Twitter feed
- Twitter allows you to link your tweets to your location. To avoid this information being recorded and shared by Twitter, turn off your “add location to your tweets” under the heading Tweet Location in your settings.


- Identifying information about phones that were accessing Twitter at that time are known to the mobile network operator. This may allow someone with access to both your Twitter feed and the operator’s records to identify you.
6. Twitter can decide to or be forced to hand over information about your account to third parties
Twitter’s privacy policy states the following:
- “We may disclose your information if we believe that it is reasonably necessary to comply with a law, regulation or legal request; to protect the safety of any person; to address fraud, security or technical issues; or to protect Twitter's rights or property.”
- A recent high-profile example is the subpoena issued to Twitter by the US government requiring that identifying information (but not actual tweets) for Twitter accounts related to or following Wikileaks.
7. Always have a backup plan
Twitter can be blocked, or experience extended downtime
Mobile network operators, Internet service providers (ISPs) and governments can block access to certain web services. Twitter is also notorious for periods of downtime. If you think this may affect you, for instance, if you are using Twitter to communicate about emergencies, consider the following tactics:
- Decide on a backup method of communication, and a meeting place
- Have a trusted contact outside the country agree to forward your communications on, either through their own account or with access to yours. Contact them by email or phone.
- Consider using a proxy to access the Internet
- Consider using Orbot (Tor on Android) to hide the source and destination of your communications. Orbot also includes a proxy service that may allow you to access blocked sites.
Security resources at Twitter.com
- Twitter’s Guidelines for Law Enforcement describe the information Twitter has about its users, and the legal procedures involved in someone else gaining access to it.
- Twitter also has a general Privacy Policy. Use the address privacy@twitter.com to ask questions or report concerns.
- There is extensive additional information on the site’s Safety Center page.

Post new comment