If you don’t want someone to know that you were accessing a particular web site (or that you were accessing it at a particular time, such as when inflammatory content was posted), you need to anonymize your mobile browsing. Depending on how your network is set up, the site you are accessing may be able to see and keep a record of your IP address. Your network administrator, Internet Service Provider and/or Mobile Network Operator can see and keep records of the IP addresses of both your Internet-connected mobile device and the sites you are accessing. IP addresses can nearly always be linked to a geographic location, whether a zip code or a city, and your ISP or mobile network provider can link your IP to your individual device.
The first part of this article - Using HTTPS for Secure Mobile Browsing - describes how mobile browsing over HTTPS provides:
- encryption for you data during transmission
- verification of the identity of the remote site
However, using HTTPS does not hide your identity. If you don’t want someone to know that you were accessing a particular web site (or that you were accessing it at a particular time, such as when inflammatory content was posted), you need to anonymize your mobile browsing. Depending on how your network is set up, the site you are accessing may be able to see and keep a record of your IP address. Your network administrator, Internet Service Provider and/or Mobile Network Operator can see and keep records of the IP addresses of both your Internet-connected mobile device and the site you are accessing. IP addresses can nearly always be linked to a geographic location, whether a zip code or a city, and your ISP or mobile network provider can link your IP to your individual device.
Organisations and countries that block websites can do so by blocking communication to and from specific IP addresses. For this reason, anonymizing your browsing is also the first step to circumventing Internet censorship.
This article describes two tactics for anonymous browsing and censorship circumvention - using a proxy, and using a mobile version of the circumvention tool Tor. Both are used on cpmputers as well as mobile devices. Specific tools for mobile phones are described in the second part of the article.
Browsing through a proxy
The simplest way to hide your identity from a remote site - and to hide the identity of the site you are accessing from your ISP or Mobile Network Operator (short, MNO) - is to browse the web through a proxy. If the proxy is located outside an organizational or national firewall, you can also use it to access sites that are blocked by the firewall.
- Proxies can be run as a subscription service, supported by advertising or provided free by sympathetic individuals and organisations.
- Proxies can be either web-based (like VirtualBrowser), where you visit a web site and enter the address of a site you want to browse anonymously.
- Another type of proxy (an HTTP or SOCKS proxy) is configurable in your browser settings and allows your web traffic is routed transparently through the proxy.
- If someone wants to run a proxy for specific individuals, they can use open source tools like web-based proxy Psiphon. Movements.org has instructions for this. Please note the caution about Psiphon below, though!
How it works
As the name suggests, a proxy performs web requests on your behalf, acting as a go-between between you and the remote site. The transaction happens like this:
- You set your browser to divert web traffic through a proxy, OR you visit a web page from which a web-based proxy is operating.
- You type in the address of the webpage you wish to visit.
- The proxy fetches the page, and returns it to your browser.
- You continue to browse as normal. Each time you click a link or type and address, the request is routed through the proxy server, which sends and receives data on your behalf.
Throughout this transaction, the remote site communicates only with the proxy server, and sees only its IP address. You, too, communicate only with the proxy server. If your communications are being monitored, the eavesdropper will not be able to tell what site you are accessing - only that you were browsing through a proxy.
Vulnerabilities
Understanding anonymous proxies is a first step towards anonymizing your browsing and being able to access blocked sites. However, proxies have some significant vulnerabilities.
- The proxy sees both your IP address and the site(s) you are accessing. You are anonymous to the remote site and the identity of the remote site is hidden from others on your network, but the proxy has all the information from both sides.
- You cannot usually independently verify the identity of the person or organisation operating a proxy, and cannot be sure they are trustworthy. This allegation has been made against Psiphon.
- A proxy is easily blocked - it is as easy to block a proxy as it is to block sites you may be trying to access through one.
- If an attacker seriously intends to observe your traffic, proxies you use are an ideal target for an attack.
For these reasons, you should not use a proxy unless you completely trust the person or organisation running the proxy. You should also ensure that all sensitive communications are encrypted by using HTTPS.
Tor
The Tor Project offers a more sophisticated way to anonymize your web browsing and other online activities. Using Tor avoids many of the problems with anonymous proxies. It is much harder to block access to Tor than to block proxies. As a decentralized, network-based system, Tor is also harder to monitor and would be harder for an attacker to control. For examples of how Tor is used by different groups of people, including law enforcement officials, journalists and activists, see this page.
How it works
Like a proxy, Tor routes data transmissions between you and the website (or other online service) you are accessing through an intermediary. Unlike a proxy, the intermediary is not a single network-connected system.
Tor has a global network of volunteers who run software that allows small amounts of traffic to be routed through their network connection, each of which is called a relay or node. When you log in to Tor and start communicating with an online service, the network randomly selects several relays to create a circuit through which your data will be transmitted.
The diagrams below (attribution: the Tor Project) illustrate this process. Alice, wanting to anonymously access an online service hosted on server Bob, uses a Tor client on her PC or mobile device. The Tor client gets a list of active Tor relays from directory server Dave, then creates a random circuit between Alice and Bob, through which their communications will be routed. When Alice wants to access a different online service hosted by Jane, the process is repeated and a new random circuit is created.
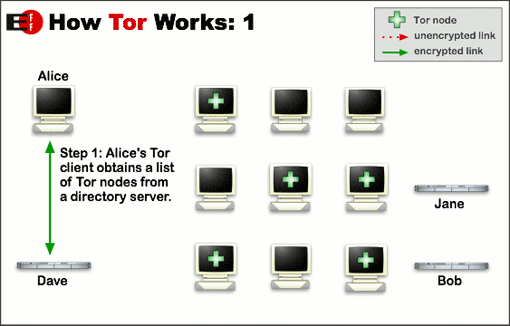
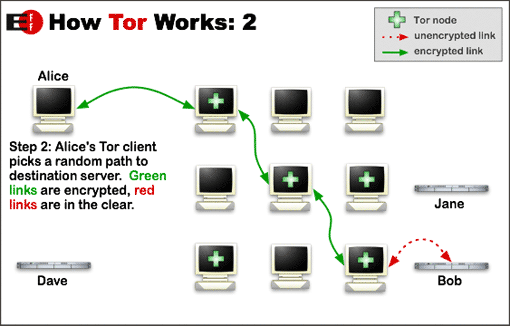
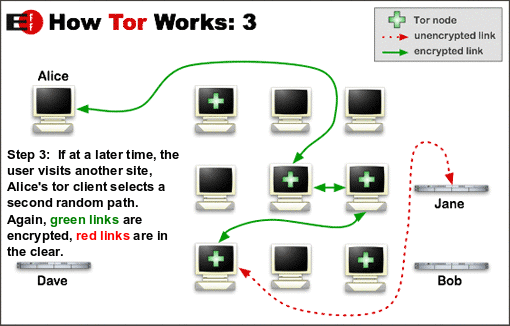
For much more information on how Tor works, see the Tor Project’s documentation archive.
Vulnerabilites
Tor may be the best option for secure web browsing in many situations, but it still doesn’t promise impenetrable security. However, Tor’s vulnerabilities are primarily ones that require extensive resources to exploit. Timing attacks occur when the attacker identifies the source of traffic on the Tor network by looking at the time it takes to send data through various different circuits. Attackers can also try to force the Tor network to route traffic through malicious nodes under their control.
The Tor Project’s Sheva Nerad had this to say about Tor vulnerabilties:
“if a person is willing to create a victim to secure their anonymity they have so [many] better options [..] botnets, identity theft, one-use cell chips, stolen equipment,… Tor remains the best option for people who need pretty good anonymity, but don’t want to create a victim to get it.”
Achieving “pretty good anonymity” still requires careful attention. Although browsing with Tor prevents your ISP or MNO from monitoring your browsing, there are many ways you can reveal your identity to web sites. These include:
- Failing to clear cookies from your web browser before browsing with Tor, and sending a cookie to the site from a previous visit when you were browsing without Tor.
- Logging in to an online service like Facebook or Gmail (although the service won’t see your location, you are obviously accessing your account)
- Using technologies like Flash, Java, JavaScript and ActiveX (full list here) to display multimedia content allows a site to run content on your device, and that code may be malicious and reveal your identity.
- Failing to use HTTPS in conjunction with Tor to encrypt and anonymize your web browsing. As shown in the diagrams above, the last link in the relay (between the exit node and the site you are accessing) is unencrypted unless you use HTTPS.
Tools
There are currently very few tools for anonymous browsing on mobile phones. Depending on what type of phone you have, you may be able to do some or all of the following:
- Use Tor (Android only)
- Use a proxy hosted by a trusted contact (any phone that can run Opera mini)
- Use a web-based proxy (any phone that can run Opera mini)
- Download your content to a PC, and post from there (any phone that can connect to a PC, but anonymous browsing only, not censorship circumvention)
Using Tor on a Mobile Phone
Orbot is the only mobile phone client officially promoted by the Tor Project. It will work on both Android 1.x and Android 2.x phones. Instructions for download and install are here.
- Orbot can be made to route web browsing and instant messaging on Android 1.x and 2.x phones through the Tor network without root access. To do this, also you’ll need to install OrWeb or Firefox for web browsing, and Gibberbot for instant messaging.
- With root access, Orbot can transparently route all traffic through the Tor network. Importantly, this includes network communications initiated from apps.
Setup takes a little time, but is straightforward. You can check that Tor is working by browsing to https://check.torproject.org/
Using an authenticated SOCKS or HTTP proxy run by a trusted contact
SOCKS and HTTP proxies can be a good option for mobile browsing if you are sure you trust the person running the proxy and their ability to keep their system secure. This should include running a proxy that requires authentication (username and password).
At the time of writing, the following options may be available depending on your phone:
- On Android, you can set a proxy in Firefox Mobile with the ProxyMob add-on . Opera Mobile may also work for some phones.
- iPhones allow a proxy to be set for WiFi only from the phone’s settings screen. Setting a proxy for mobile Internet traffic (GPRS, 3G etc) is possible with some technical effort - see these: Guide 1 and Guide 2.
Use Opera Mini
Opera Mini is available for many phones, including Java phones. Opera Mini doesn’t allow you to set your own proxy, but it does route all your web traffic through its own server. This may mean you are able to access otherwise blocked sites when browsing with Opera Mini. The tradeoff is that you need to trust Opera Software with your information, as they can see all traffic routed through their servers.
Using a Web-Based Proxy Run by a Trusted Contact
Most mobile browsers should have no trouble with web-based proxies, although some content may not display correctly.
Alternatives for Anonymous Content Uploading
If you aren’t able to use the suggestions above, your best option for uploading content from your mobile without revealing your identity is probably to first transfer the content to a secured computer. From there, use Tor to upload your media. There are many guides to anonymous browsing available online, but here are some links to get you started:
- Protektor Services’ free, cross-platform security manuals
- Tor guide from Security-in-a-box (including Tor browser bundle)
- Anonymous blogging with Wordpress and Tor
If you don’t want someone to know that you were accessing a particular web site (or that you were accessing it at a particular time, such as when inflammatory content was posted), you need to anonymize your mobile browsing. Depending on how your network is set up, the site you are accessing may be able to see and keep a record of your IP address. Your network administrator, Internet Service Provider and/or Mobile Network Operator can see and keep records of the IP addresses of both your Internet-connected mobile device and the sites you are accessing. IP addresses can nearly always be linked to a geographic location, whether a zip code or a city, and your ISP or mobile network provider can link your IP to your individual device.
The first part of this article - Using HTTPS for Secure Mobile Browsing - describes how mobile browsing over HTTPS provides:
- encryption for you data during transmission
- verification of the identity of the remote site
However, using HTTPS does not hide your identity. If you don’t want someone to know that you were accessing a particular web site (or that you were accessing it at a particular time, such as when inflammatory content was posted), you need to anonymize your mobile browsing. Depending on how your network is set up, the site you are accessing may be able to see and keep a record of your IP address. Your network administrator, Internet Service Provider and/or Mobile Network Operator can see and keep records of the IP addresses of both your Internet-connected mobile device and the site you are accessing. IP addresses can nearly always be linked to a geographic location, whether a zip code or a city, and your ISP or mobile network provider can link your IP to your individual device.
Organisations and countries that block websites can do so by blocking communication to and from specific IP addresses. For this reason, anonymizing your browsing is also the first step to circumventing Internet censorship.
This article describes two tactics for anonymous browsing and censorship circumvention - using a proxy, and using a mobile version of the circumvention tool Tor. Both are used on cpmputers as well as mobile devices. Specific tools for mobile phones are described in the second part of the article.
Browsing through a proxy
The simplest way to hide your identity from a remote site - and to hide the identity of the site you are accessing from your ISP or Mobile Network Operator (short, MNO) - is to browse the web through a proxy. If the proxy is located outside an organizational or national firewall, you can also use it to access sites that are blocked by the firewall.
- Proxies can be run as a subscription service, supported by advertising or provided free by sympathetic individuals and organisations.
- Proxies can be either web-based (like VirtualBrowser), where you visit a web site and enter the address of a site you want to browse anonymously.
- Another type of proxy (an HTTP or SOCKS proxy) is configurable in your browser settings and allows your web traffic is routed transparently through the proxy.
- If someone wants to run a proxy for specific individuals, they can use open source tools like web-based proxy Psiphon. Movements.org has instructions for this. Please note the caution about Psiphon below, though!
How it works
As the name suggests, a proxy performs web requests on your behalf, acting as a go-between between you and the remote site. The transaction happens like this:
- You set your browser to divert web traffic through a proxy, OR you visit a web page from which a web-based proxy is operating.
- You type in the address of the webpage you wish to visit.
- The proxy fetches the page, and returns it to your browser.
- You continue to browse as normal. Each time you click a link or type and address, the request is routed through the proxy server, which sends and receives data on your behalf.
Throughout this transaction, the remote site communicates only with the proxy server, and sees only its IP address. You, too, communicate only with the proxy server. If your communications are being monitored, the eavesdropper will not be able to tell what site you are accessing - only that you were browsing through a proxy.
Vulnerabilities
Understanding anonymous proxies is a first step towards anonymizing your browsing and being able to access blocked sites. However, proxies have some significant vulnerabilities.
- The proxy sees both your IP address and the site(s) you are accessing. You are anonymous to the remote site and the identity of the remote site is hidden from others on your network, but the proxy has all the information from both sides.
- You cannot usually independently verify the identity of the person or organisation operating a proxy, and cannot be sure they are trustworthy. This allegation has been made against Psiphon.
- A proxy is easily blocked - it is as easy to block a proxy as it is to block sites you may be trying to access through one.
- If an attacker seriously intends to observe your traffic, proxies you use are an ideal target for an attack.
For these reasons, you should not use a proxy unless you completely trust the person or organisation running the proxy. You should also ensure that all sensitive communications are encrypted by using HTTPS.
Tor
The Tor Project offers a more sophisticated way to anonymize your web browsing and other online activities. Using Tor avoids many of the problems with anonymous proxies. It is much harder to block access to Tor than to block proxies. As a decentralized, network-based system, Tor is also harder to monitor and would be harder for an attacker to control. For examples of how Tor is used by different groups of people, including law enforcement officials, journalists and activists, see this page.
How it works
Like a proxy, Tor routes data transmissions between you and the website (or other online service) you are accessing through an intermediary. Unlike a proxy, the intermediary is not a single network-connected system.
Tor has a global network of volunteers who run software that allows small amounts of traffic to be routed through their network connection, each of which is called a relay or node. When you log in to Tor and start communicating with an online service, the network randomly selects several relays to create a circuit through which your data will be transmitted.
The diagrams below (attribution: the Tor Project) illustrate this process. Alice, wanting to anonymously access an online service hosted on server Bob, uses a Tor client on her PC or mobile device. The Tor client gets a list of active Tor relays from directory server Dave, then creates a random circuit between Alice and Bob, through which their communications will be routed. When Alice wants to access a different online service hosted by Jane, the process is repeated and a new random circuit is created.



For much more information on how Tor works, see the Tor Project’s documentation archive.
Vulnerabilites
Tor may be the best option for secure web browsing in many situations, but it still doesn’t promise impenetrable security. However, Tor’s vulnerabilities are primarily ones that require extensive resources to exploit. Timing attacks occur when the attacker identifies the source of traffic on the Tor network by looking at the time it takes to send data through various different circuits. Attackers can also try to force the Tor network to route traffic through malicious nodes under their control.
The Tor Project’s Sheva Nerad had this to say about Tor vulnerabilties:
“if a person is willing to create a victim to secure their anonymity they have so [many] better options [..] botnets, identity theft, one-use cell chips, stolen equipment,… Tor remains the best option for people who need pretty good anonymity, but don’t want to create a victim to get it.”
Achieving “pretty good anonymity” still requires careful attention. Although browsing with Tor prevents your ISP or MNO from monitoring your browsing, there are many ways you can reveal your identity to web sites. These include:
- Failing to clear cookies from your web browser before browsing with Tor, and sending a cookie to the site from a previous visit when you were browsing without Tor.
- Logging in to an online service like Facebook or Gmail (although the service won’t see your location, you are obviously accessing your account)
- Using technologies like Flash, Java, JavaScript and ActiveX (full list here) to display multimedia content allows a site to run content on your device, and that code may be malicious and reveal your identity.
- Failing to use HTTPS in conjunction with Tor to encrypt and anonymize your web browsing. As shown in the diagrams above, the last link in the relay (between the exit node and the site you are accessing) is unencrypted unless you use HTTPS.
Tools
There are currently very few tools for anonymous browsing on mobile phones. Depending on what type of phone you have, you may be able to do some or all of the following:
- Use Tor (Android only)
- Use a proxy hosted by a trusted contact (any phone that can run Opera mini)
- Use a web-based proxy (any phone that can run Opera mini)
- Download your content to a PC, and post from there (any phone that can connect to a PC, but anonymous browsing only, not censorship circumvention)
Using Tor on a Mobile Phone
Orbot is the only mobile phone client officially promoted by the Tor Project. It will work on both Android 1.x and Android 2.x phones. Instructions for download and install are here.
- Orbot can be made to route web browsing and instant messaging on Android 1.x and 2.x phones through the Tor network without root access. To do this, also you’ll need to install OrWeb or Firefox for web browsing, and Gibberbot for instant messaging.
- With root access, Orbot can transparently route all traffic through the Tor network. Importantly, this includes network communications initiated from apps.
Setup takes a little time, but is straightforward. You can check that Tor is working by browsing to https://check.torproject.org/
Using an authenticated SOCKS or HTTP proxy run by a trusted contact
SOCKS and HTTP proxies can be a good option for mobile browsing if you are sure you trust the person running the proxy and their ability to keep their system secure. This should include running a proxy that requires authentication (username and password).
At the time of writing, the following options may be available depending on your phone:
- On Android, you can set a proxy in Firefox Mobile with the ProxyMob add-on . Opera Mobile may also work for some phones.
- iPhones allow a proxy to be set for WiFi only from the phone’s settings screen. Setting a proxy for mobile Internet traffic (GPRS, 3G etc) is possible with some technical effort - see these: Guide 1 and Guide 2.
Use Opera Mini
Opera Mini is available for many phones, including Java phones. Opera Mini doesn’t allow you to set your own proxy, but it does route all your web traffic through its own server. This may mean you are able to access otherwise blocked sites when browsing with Opera Mini. The tradeoff is that you need to trust Opera Software with your information, as they can see all traffic routed through their servers.
Using a Web-Based Proxy Run by a Trusted Contact
Most mobile browsers should have no trouble with web-based proxies, although some content may not display correctly.
Alternatives for Anonymous Content Uploading
If you aren’t able to use the suggestions above, your best option for uploading content from your mobile without revealing your identity is probably to first transfer the content to a secured computer. From there, use Tor to upload your media. There are many guides to anonymous browsing available online, but here are some links to get you started:
- Protektor Services’ free, cross-platform security manuals
- Tor guide from Security-in-a-box (including Tor browser bundle)
- Anonymous blogging with Wordpress and Tor

Post new comment